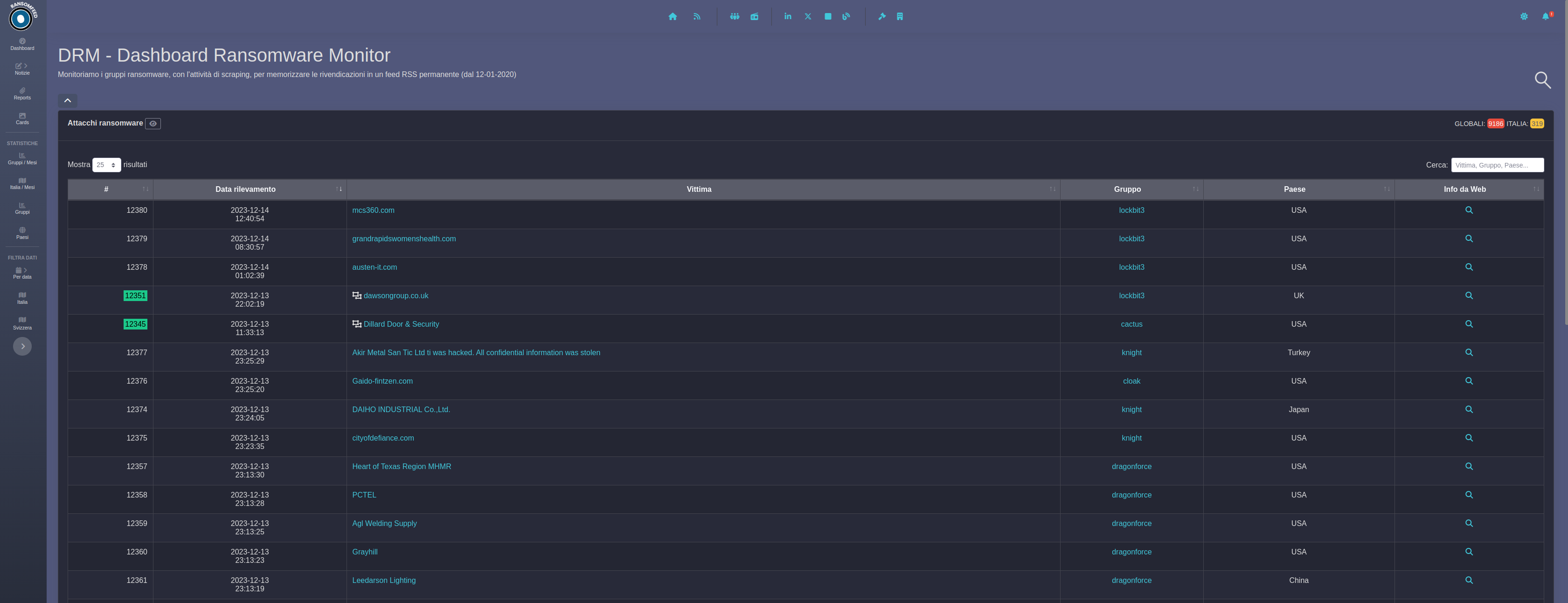
EriZone Servicedesk: Upgrade to RockyLinux9/RHEL9 (CentOS7 EOL in June 2024)!
Dear EriZone customers! Our legacy servicedesk system EriZone currently runs on CentOS7 or Red Hat Enterprise Linux (RHEL) 7. These operating systems will not get any security fixes after June 2024. For anyone planning on keeping EriZone running beyond this date, we highly recommend you contact us for an upgrade to Rocky Linux 9. As…
Read More