Now It’s Really Easy to Activate OTP for Your Personal NetEye Account
It’s really easy now to activate OTP on your personal account with NetEye with our new authentication method. In the latest 4.38 version of NetEye we’ve introduced a new product to manage authentication (documentation here).
In the future thanks to this new product we’ll be able to define the various actions that each user can carry out within NetEye across the various modules in our system.
The use case I wanted to try was to enable OTP for a specific user defined in NetEye, either local or domain. So my goal, is: enable OTP for my user.
At its core, an OTP (One-Time Password) is a temporary, single-use code that’s generated for a specific login session or transaction. Unlike traditional passwords, which are static and can be reused until changed, OTPs are dynamic and expire either after a short time or once they’re used. This simple yet effective mechanism makes OTPs a critical layer in modern authentication systems.
Delivered through SMS, email, or even dedicated authentication apps like Google Authenticator, OTPs have significantly raised the bar for secure user verification. They play a central role in multi-factor authentication (MFA), reinforcing the protection of our sensitive data.
Why Have OTPs Become Essential?
Cybersecurity threats are evolving, and so must our defenses. Here’s a quick overview of why OTPs became so critical:
- The Increasing Sophistication of Cyberattacks: Cybercriminals are more advanced than ever. Phishing, credential theft, and keystroke logging are just a few examples of attacks that target static passwords. OTPs add an extra layer of security by ensuring that even if a static password is compromised, the attacker will still need the one-time code.
- Regulatory Requirements: We all know the headaches that regulatory compliance can bring, especially with standards like GDPR, HIPAA, and PCI DSS. These standards often require the implementation of MFA to safeguard sensitive data, and OTPs fit this need perfectly.
- Consumer Trust and Business Continuity: Businesses live and die by their reputation. One data breach can cause irreparable damage, especially when dealing with sensitive consumer data. OTPs help protect the trust we’ve built by adding an extra barrier between attackers and our systems.
- Rise of Mobile Technology: With the explosion of mobile devices, delivering OTPs via SMS, email, or push notifications has become not only possible, but even convenient. Authentication apps now allow for real-time OTP generation directly on users’ devices, improving both security and the user experience.
After realizing the importance of enabling OTP, reading a bit of documentation and doing some testing, here’s the procedure I use for enabling an OTP user account.
Step 1: Create a Test User
I connect as root to my NetEye and go to the authentication section as shown below:
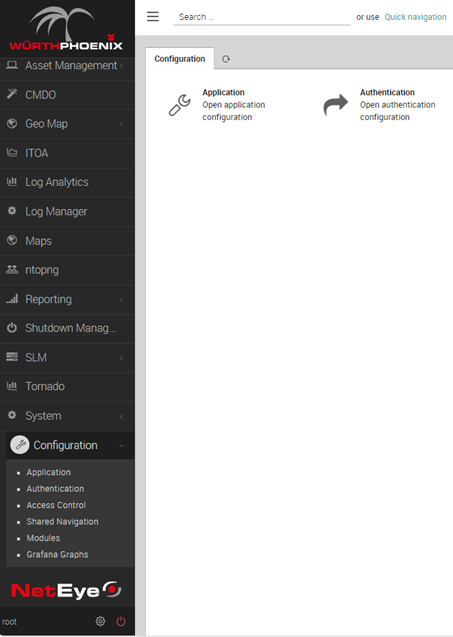
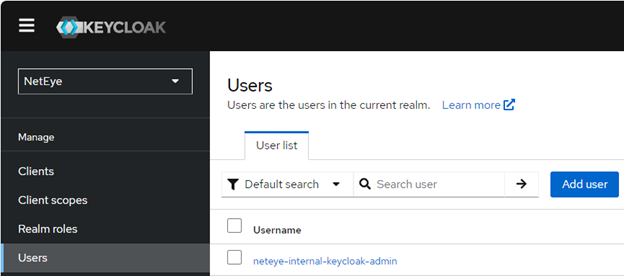
Then I access our authentication system and click on Users and Add user:
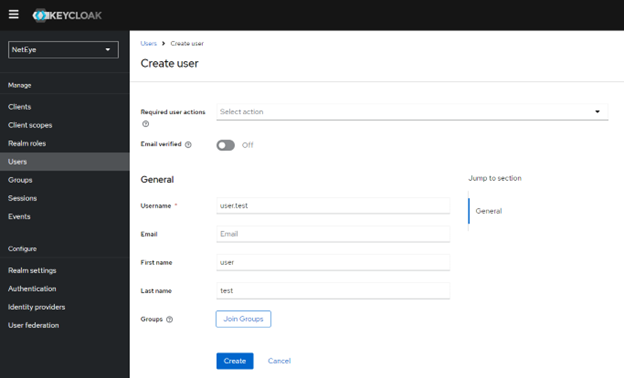
Next, I fill in the fields by entering the username and clicking on Create:
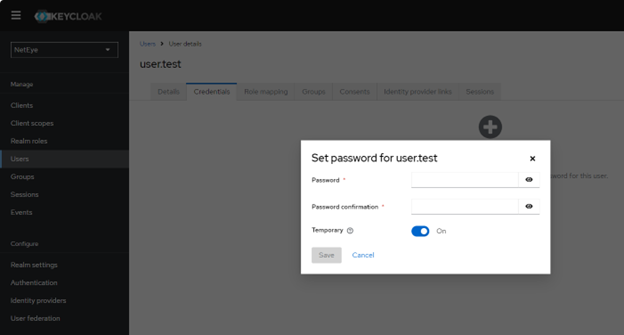
After creating the user account, I click on the Credential tab and add a password. I then decide whether it should be temporary or permanent:
I set the password and try to connect to NetEye with the new anonymous user:
Since I don’t have an associated role, I don’t see any modules, but my goal is to enable OTP. So I reopen the authentication section, search for the newly created user account and edit it again. In the Required user action part, I add Configure OTP:
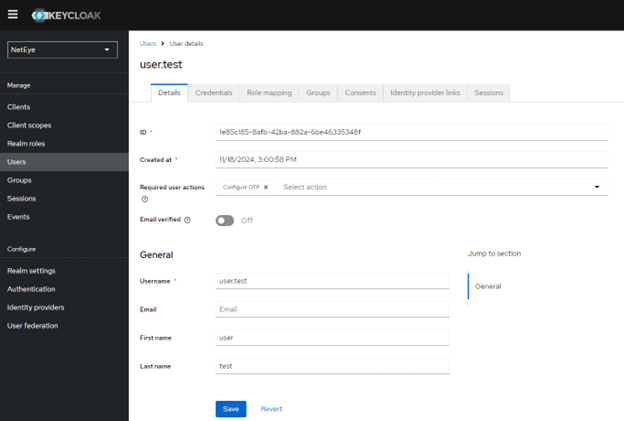
Then I save and log out. Now I try to log in again by entering my user name and password:

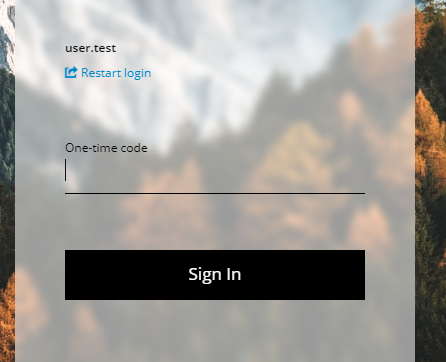
I select Google Authenticator and configure the device, enter the code and click submit. Then I disconnect and reconnect; after entering the username and password I’m now prompted for OTP.
Voilà I’ve reached my goal:
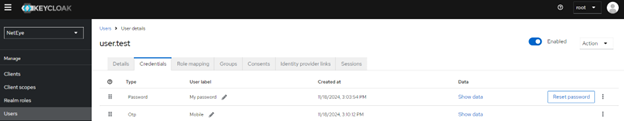
The same thing can also be done with a domain-defined user on which I enable OTP in the configuration. If I want to remove it, I simply delete the OTP code in the credentials:
To remove it from Google Authenticator was more complicated. Google’s guides aren’t very helpful, but in the end I succeeded.
If you encounter any problems, please contact me, it’s a small-scale challenge 😊






