
Double extortion ransomware attacks have reached very high numerical values. One of the key elements, when suffering such an attack, concerns the negotiation that can be initiated (not always!) with the ransomware gang. The analysis, carried out by the SEC4U team, of hundreds of negotiations makes it possible to apply a scientific approach to this fundamental phase.
The database from which we started to carry out this analysis is the Ransomchat project (https://github.com/Casualtek/Ransomchats) by Valéry Marchive, whom we thank. Within the project, 122 ransomware gang chats were collected, listed below (the name of the ransomware gang and the number of chats analyzed for each gang is given):
- Akira: #6
- Avaddon: #7
- Avos: #1
- Babuk: #2
- BlackMatter: #2
- Conti: #32
- Darkside: #5
- Hive: #8
- Lockbit3.0: #36
- MountLocker: #1
- Ranzy: #2
- REvil: #20
A quick summary of the macro phases that are present within a ransomware attack:

- Phase 1: Reconnaissance and target selection.
- Phase 2: Initial access.
- Phase 3: Lateral movement and privilege escalation.
- Phase 4: Deployment of ransomware payload.
- Phase 5: Encryption and impact.
- Phase 6: Extortion and communication.
The objective of our research was to analyze in depth phase 6: “Extortion and Communication,” focusing on the aspects related to negotiation that can occur during this stage.
What is Negotiation?
Negotiation is an interpersonal decision-making process that becomes necessary when it’s not possible to achieve one’s goals unilaterally.
The negotiator is the entity, one for each party, who conducts the negotiation.
Negotiation during a ransomware attack typically takes place in a restricted-access chat.
There are 3 different types of negotiation in the literature:
- competitive
- cooperative
- integrative
Let’s now look together at the important elements of the 3 different types of negotiations.
Competitive Negotiation
- Has the objective of obtaining an agreement that is advantageous for itself and disadvantageous for the other party
- Intimidate the opponent
- Make him lose faith in his own negotiating skills
- Force him to accept the agreement even if it is more disadvantageous than expected

Cooperative Negotiation
- Try to reach an agreement that is satisfactory for both parties
- Try to build a relationship with the other party, based on trust
- The negotiation must begin with concessions and proceed with moderate requests that are generally easily accepted by the opponent
- It works especially when both parties adopt it
Integrative Negotiation
- Combines the 2 approaches
- Both parties try to get as many concessions as possible from the other party
- As in the cooperative approach, the litigants attempt to reach an amicable settlement to the dispute
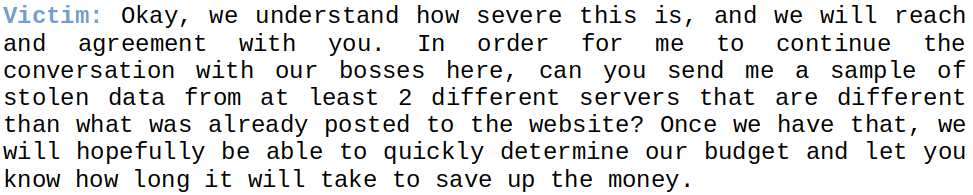
Why Negotiate (Which is Different from Paying)?
Obviously, we would never go so far as to suggest paying a ransom to a ransomware gang, as this only funds other illicit activities by the ransomware gang itself, but we certainly believe it is critical that any organization have the ability to secure alternative scenarios for handling the attack, because:
- At the beginning of an Incident Response process it is not clear what the ending might be.
- Why should I close all contact with the Threat Actor?
- What do I have to lose by contacting the Threat Actor?
- What if paying the ransom is the only viable choice to give your business a future?

Assumptions
Below we specify some assumptions that are good to know when faced with the need to handle ransomware attacks:
- The ransom amount is not decided randomly
- The Threat Actor:
- doesn’t like negotiators
- wants our money
- invests money to attack
- needs our money

Our IR Team
There is an Incident Response team within our Security Operations Center that, by virtue of its experience, has decided to point out a list of recommendations of do’s and don’ts during a ransomware-related negotiation activity.
Dos!
Here are the things we suggest handling during a negotiation:
- Do stay calm and patient (which is the virtue of the strong!)
- Do maintain a professional and respectful tone
- Do show empathy towards the Threat Actor’s situation and objectives
- Do make it clear to the other party that he is talking to the person who (or who is close to whom) can make decisions
- Do try to establish “tactical empathy” by mirroring the hacker’s language patterns
- Do look for information about the gang that attacked your organization. You need to know the counterparty’s reputation in order to best deal with it
- Do ask for proof of the correct functioning of the decryptor, both on small and large files
- Do make sure the negotiation chat is secure (AKA the private link has not been shared)
- Do prepare communications (precise, complete, and transparent) for the various stakeholders
Don’ts!
Instead, here are the things we absolutely recommend you not do during a negotiation!
- Don’t try to fix the situation on your own. Involve relevant authorities and experts. Negotiation is not a theme to be improvised!
- Don’t share personal or confidential information with the gang. Just discuss the specific data and ransom situation.
- Don’t mention any involvement of insurance companies
- Don’t threaten or provoke the Threat Actor. This could make the situation even more tense and damaging.
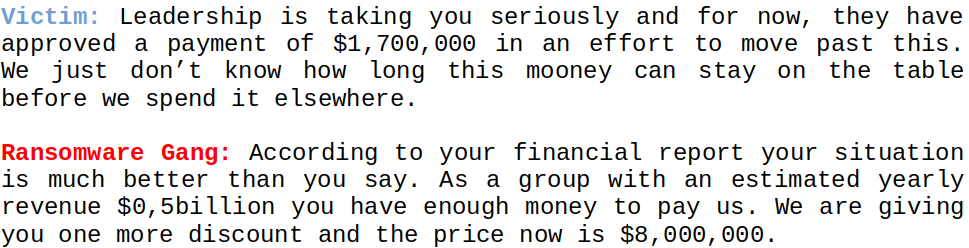
Our Analysis
We will now move on to carefully analyze the results of our analysis, going into detail about the ransom chats analyzed:

- 122 ransomware chats analyzed
- 29 of these resulted in payment by the victim organization
- 93 did not lead to payment
Python Script to Automate Analysis
To automate our analysis as much as possible we wrote a script in Python that reports in output, for each ransomware gang:
- The aggressiveness index of the ransomware gang in case of payment made
- The aggressiveness index of the victim in case of payment
- The aggressiveness index of the ransomware gang in case of non-payment
- The aggressiveness index of the victim in case of non-payment
- The duration of the negotiation in case of payment
- The duration of the negotiation in case of non-payment
- Special characters “!” and “?” used by the ransomware gang
- Special characters “!” and “?” used by the victim
- The words most used by the ransomware gang
- The words most used by the victim
- Any similarities between the phrases used within the various ransom chats
- The average number of words present in the ransomware gang’s sentences
- The average number of words present in the victim’s sentences
- Ransom chat number in which the payment occurred
- Ransom chat number in which the payment did not take place
These elements, if carefully analyzed, can allow us to identify the typical tactics used during negotiations and to inspire important ideas to better manage future negotiations.
Here is a sample of the output for the Conti gang ransomware:
$ index Victim: -38 #15
$ index Conti: 160 #15
not$ index Victim: -153 #17
not$ index Conti: 290 #17
$ delta: 17 #15
not$ delta: 25 #17Aggressiveness Index
Based on the words used in communications, we drew up 2 lists:
- 1 of aggressive words
- 1 of non-aggressive words.
We therefore calculated, for the Threat Actor and for the Victim, an aggressiveness index for the various communications.
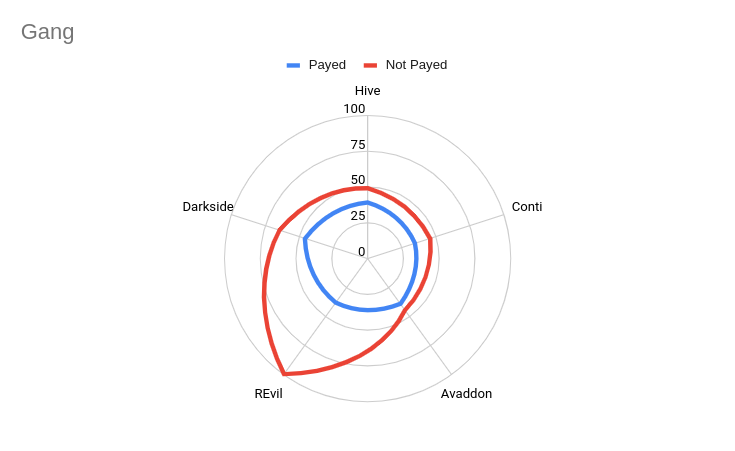
Aggressiveness index – Focus on Gangs
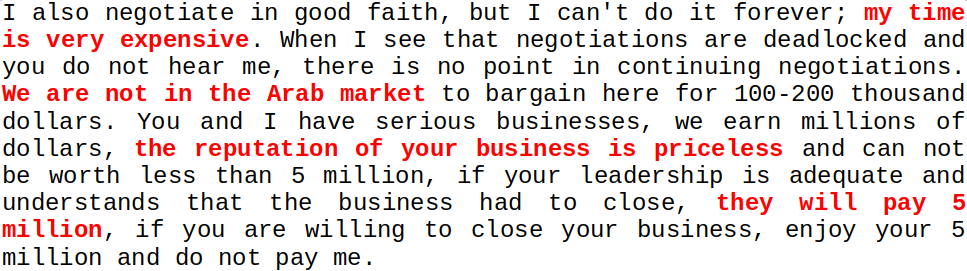
The analysis, as is clear from the chart below, led us to understand that the ransomware gang tends to use more aggressive language as the negotiation gets longer and it becomes more difficult to come to an agreement related to ransom.
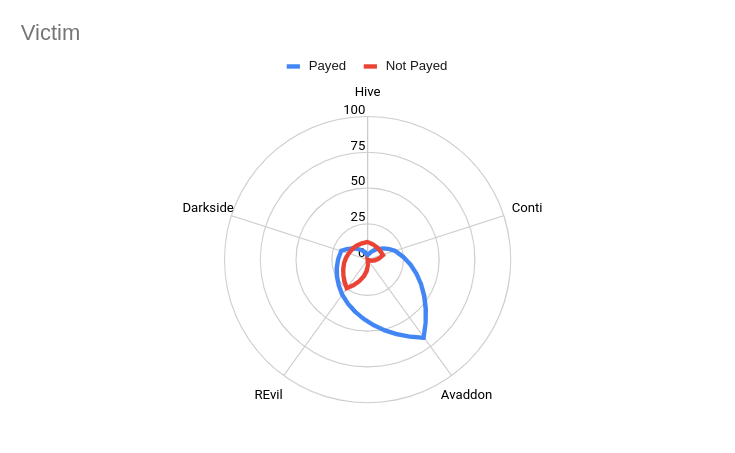
Aggressiveness index – Focus on Victims
The analysis, as shown in the graph below, led us to understand that the victim tends to use more aggressive language during negotiations leading to a ransomware-related agreement with the ransomware gang.
Most Frequently Used Words
Below we provide evidence of the most frequently used words within ransomware chats by ransomware gangs and victims, respectively:
Ransomware gangs’ words:
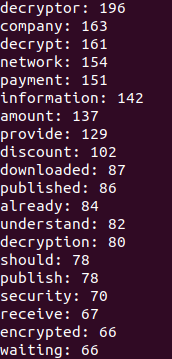
Victims’ words:
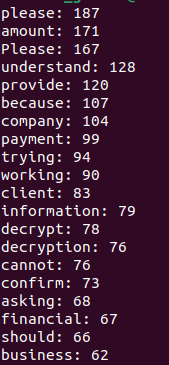
Repeated Phrases
We detected some repeated phrases, even within different gang ransom chats. This potentially indicates 2 things:
- Potential links between different gangs
- Study of negotiation techniques of one ransomware gang by another
Below we show the most important identical phrases detected:
1) Hello and welcome to Hive. How may I help you?
2) The price is not a subject to discuss.
3) You need pay for decrypt your files. Your price is $xxxxxx.
4) We will also try to find a buyer for your data and access to your network if you refuse to pay.
5) Your offer has been rejected. Make a realistic offer based on our offer.
6) We will send you 30% of the file tree, you will select any 3 pcs of non-sensitive information and we will provide them to you as evidence.
7) Evaluate our steps. You can negotiate with us. But offering funny amounts is not the best way for you. It leads to publication.
8) Make a reasonable offer based on our offer.
9) Well, we are waiting, do not delay, this will entail negative consequences of publication.
10) Then we will not be able to agree.
11) Let's not delay the negotiations. This has a negative effect on the fact of publishing you. Be more active.Focus on Conti Ransomware Gang Chats
We later focused on Threat Actor Conti’s ransom chats, as there is an excellent number of chats from this ransomware gang to analyze, both among those that led to an agreement between the parties and those that did not.
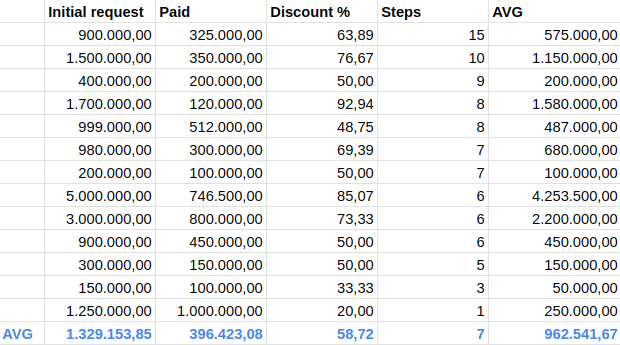
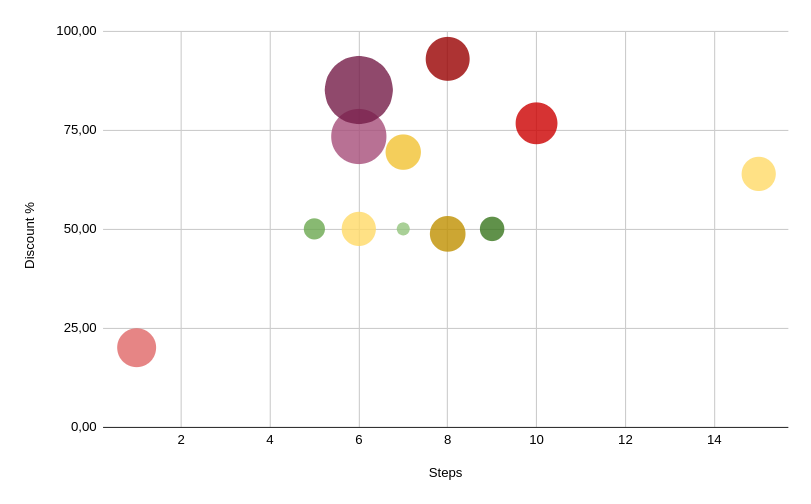
As we can see from the chart below, the moment the negotiation succeeds in achieving its purpose, that is, to initiate a constructive discussion between the parties during which the negotiation steps are many, it is then that agreements can be found that are decidedly different compared to the initial request.
Indeed, in the 13 ransom chats of the Conti ransomware gang that were analyzed, there was an average savings of over $900,000 and an average number of 7 negotiation steps. On average in the negotiations in which the steps were higher (i.e., equal to or above the average) there were the highest discount percentages compared to the initial ransom demand.
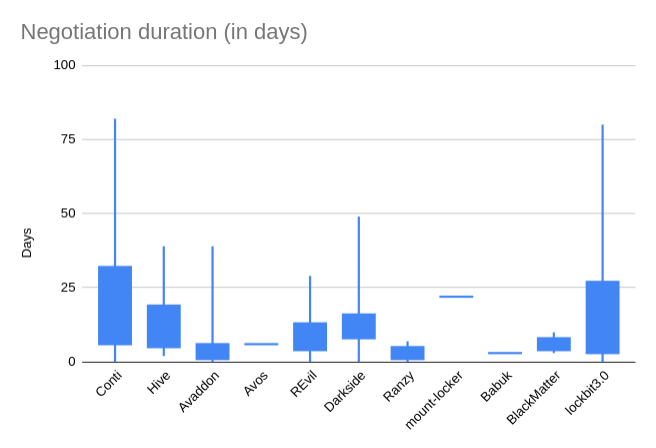
Negotiation Duration
Another element we want to show concerns the duration of negotiations. We can see that the Conti and Lockbit groups historically have been the Threat Actors who have undertaken the longest negotiations.
Negotiation is a fundamental activity, which allows you to increase the number of communication steps (and consequently the possibility of obtaining better conditions) with the ransomware gang.







