That Time I Brought a Velociraptor and a Chainsaw into the SOC

Yes, you read that title right. Today I’m going to tell you about the time I went on a hunt to bring a velociraptor and a chainsaw into the Würth Phoenix Security Operations Center. I know that it might sound strange to many and few will believe it, but I’m sure that once you get to the bottom of this article I’ll have managed to convince you that it really did happen.
Now that I’ve caught your attention, I probably have to admit that these are neither a giant green lizard nor a chainsaw with a motor and saw teeth. These are two tools that are widely used in the field of Digital Forensics and Incident Response. In fact, Würth Phoenix offers a dedicated service in case of security incidents, providing assistance in a timely manner 24/7. For more information you can consult the dedicated page on the official website at the following link: Incident Response.
Velociraptor
Velociraptor is a very powerful digital forensics and incident response tool that enhances visibility into endpoints. More precisely, Velociraptor allows data to be collected from connected endpoints, monitor their activities and perform targeted searches called ‘hunts’. But before analyzing these functionalities in more detail, it’s necessary to understand how this tool works and how to make it operational.
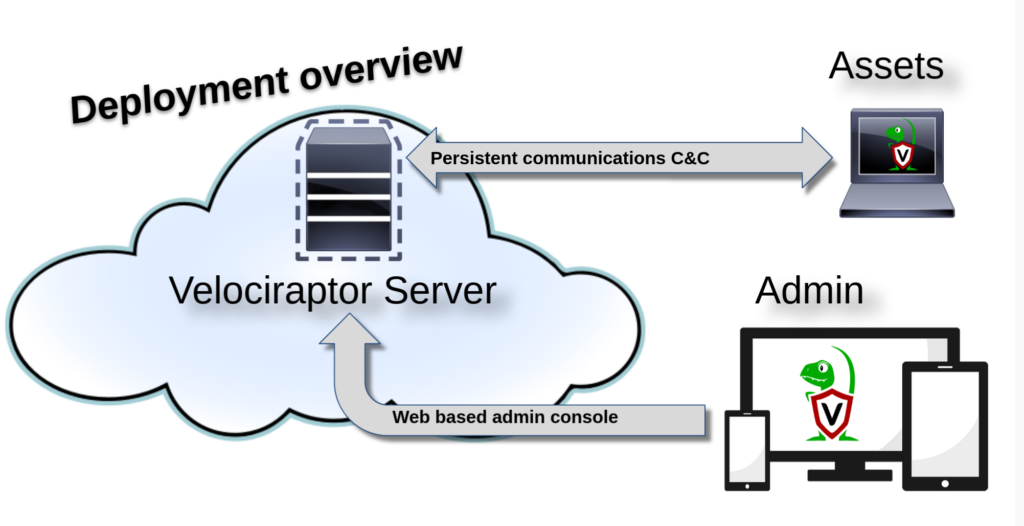
Deployment
To deploy Velociraptor, a machine must be dedicated and configured as a server. The deployment process begins with the installation of the Velociraptor agent on the server to generate configuration files. These configuration files are created in two versions, one for the server and one for the clients, within which crucial information such as the server’s IP address, data storage mode and console login credentials are included.
Once the configuration files have been generated, they are distributed to the target endpoints together with the Velociraptor agent, which can easily be done via GPO. This allows the endpoints to connect to the server and be monitored.
When agents are started on both the server and endpoints, a persistent communication channel (C2) is established between the server and each endpoint. This channel ensures a secure flow of data, allowing continuous communication between the server and the monitored machines. In addition, the administrative web console becomes accessible to the created admin users, allowing them to manage and analyze the collected data.
Collect, Monitor and Hunt
With the deployment part out of the way, we can go and see Velociraptor’s potential at work. It’s important to note that there are so many features that it’s impossible to analyze them all, so I’ll limit myself to showing just basic operations from which more specific, targeted and complex operations can be developed later.
The main use that can be made of Velociraptor is to collect events from endpoints: this can be done in different ways and for different purposes. A very simple example is to virtualize the file system of an endpoint in order to be able to browse it and ‘collect’ the files or information which you are interested in with complete freedom. This option provides an overview of the machine and allows one to explore each path in search of relevant information, even ignoring the precise location. On the other hand, this can only be done on one host at a time, and when the number of hosts increases, it’s certainly won’t be the right solution.
Alternatively, ‘Artifacts’ can be used, that is, predefined modules/scripts represented by a set of instructions that Velociraptor executes to gather specific information from endpoints, such as system logs, network configurations, log files, running processes, and more. The artifacts are in YAML format and can include queries to gather specific information, system commands, and parsing functions. By executing an artifact, the instructions defined in the script are sent to the agent installed on the endpoints, which executes the instructions, collecting the required data and sending it back to the Velociraptor server.
Of course, artifacts can be customized to collect specific data or be created from scratch. They can be automated to save time and perform monitoring tasks, but most importantly, they are modular so they can be integrated with each other according to specific needs.
The possibility of scheduling the execution of certain artifacts makes it possible to carry out monitoring activities. In fact, the possibility of periodic execution and the possibility of ‘active monitoring’ always provides up-to-date data in line with what’s happening on the hosts.
A very important note is the existence of a Velociraptor community behind the creation of artifacts. In fact it’s possible to both take inspiration from and use artifacts written by someone else, or share your own artifacts used for specific information. All this is done on the official documentation in the Artifact Exchange.
Chainsaw
Chainsaw is another tool used in the DFIR environment with ‘first-response’ capabilities, but these are limited to Windows events. In fact, it allows quick searches within Windows event logs by means of specific keywords or by using detection rules, including the much-loved Sigma rules.
Chainsaw offers 2 main features:
- Search: allows logs to be analyzed for specific keywords
- Hunt: allows logs to be analyzed via specific rules, enabling the use of more complex but at the same time more targeted filters
Chainsaw’s strength is its versatility and efficiency. In a very quick and simple way, it allows a large number of logs to be analyzed at the same time, enabling investigators to identify relevant events without having to manually analyze large volumes of data. It allows for customization of the analysis from every point of view by providing an advanced filtering system: in addition to keyword search it allows the use of regex or tau expressions, it can filter events by timestamp or event timezone, and it can even consider only files with a certain extension or a certain date.
In short, it offers the greatest possible level of freedom, and if that were not enough, it’s compatible with Sigma Rules, via a dedicated mapping file, making it possible to search for certain patterns and specific threats by correlating events, which would be impossible to identify by a manual search.
Analysis results can be exported in different formats, such as JSON and CSV, to facilitate reporting and integration with other analysis tools.
Final Thoughts and Next Steps
In conclusion, I hope I’ve convinced you that the initial statement wasn’t a lie: I have actually brought a Velociraptor and a Chainsaw to the office, even if in the form of Digital Forensic and Incident Response tools, just not in the way everyone expected, unfortunately.
This article aimed to introduce these two tools, highlighting their main features and the huge potential they can offer to those working in this field. I hope to have provided a clear and inspirational overview, and perhaps in the future there will be an opportunity to explore some advanced functionalities in more detail, or even to analyze some concrete use cases.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.






