While traditional vulnerability scanning techniques provide valuable insights from the outside, authenticated scans offer a deeper, more comprehensive understanding of system security by providing more vulnerability details on the scanned system from an internal perspective.
By leveraging valid system credentials, Greenbone’s authenticated scans provide critical insights about system configurations, software versions, and potential internal weaknesses that could be exploited by internal attackers in addition to the externally visible vulnerabilities.
How Authenticated Scan Works
During this type of scan the Greenbone appliance logs into the system using the configured credentials and runs local security checks that should not cause any malfunctions or unwanted behavior since they are designed to be safe and non-invasive, focusing on reading configurations and identifying vulnerabilities without modifying the system.
In any event there may be some performance issues or, if the credentials provided have administrative or root privileges, the appliance may access critical resources, which is never a good practice.
The credentials to use in these scans must be created in the Configurations tab and then Credentials:
After entering a Username and Password (e.g., for SSH or SMB) of a valid user and setting the other configuration parameters (Allow insecure login if the appliance can use the credential for unencrypted or insecure authentication methods, or Auto-generate if the appliance creates a random password), use the credentials while configuring the Greenbone target:
Different types of credentials can be used for authenticated checks based on the nature of the target:
- SMB to check the patch level and installed software on Microsoft Windows systems
- SSH to check the patch level on Unix and Linux systems
- ESXi to test VMware ESXi servers locally
- SNMP to test network components
An authenticated scan is similar to a white box approach, since the appliance can access the target, especially its registry, software versions and patch levels. An example is the following result that was detected by an authenticated scan test (while the same scan on the same machine without configured credentials did not detect it):
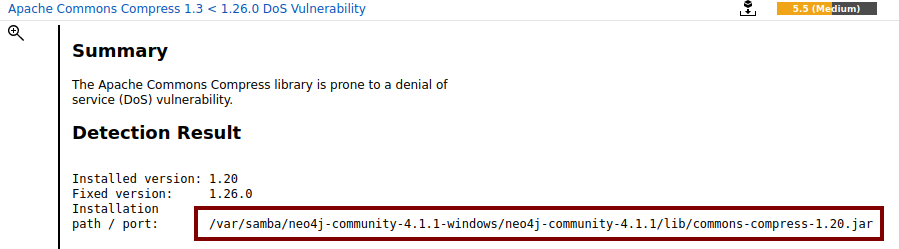
For a successful authenticated scan, some requirements must be met depending on the target systems. The main ones are reported here for Microsoft Windows systems, and here for Linux/Unix targets.
Concluding Insights
With this blog post, I’d like to point out and highlight the presence of this additional functionality offered by Greenbone, that is, to run authenticated scans for deeper checks and discover vulnerabilities that require privileged access, such as internal configuration issues or vulnerable applications.
Even though the Local Security Checks performed by Greenbone during an authenticated scan shouldn’t cause any malfunctions, it’s always recommended to monitor the performance of the target system and to first perform tests on staging products to verify the response capacity.
During our tests, no disruptions or other relevant problems were detected except for the longer duration of the authenticated scans compared to the same scan without credentials, especially for Windows systems. It should also be noted that if the full and fast scan config is in place, only those vulnerability tests that are safe (safe_checks set to yes) will be executed.
In conclusion, authenticated scans with Greenbone provide critical insights by uncovering vulnerabilities that are typically missed in traditional, non-authenticated automated scans.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







