On 19 February, through an operation coordinated by the National Crime Agency (NCA), a large part of the infrastructure of the Lockbit ransomware gang was seized.
The ransomware gang, active since 2019, is undoubtedly best known within the field of double extortion ransomware attacks, having published claims relating to 2,591 attacked organizations over the years.
The seizure message appears on the various mirrors of the Ransomware Gang’s Data Leak Site (DLS), the list of which is available within our deepdarkCTI project.

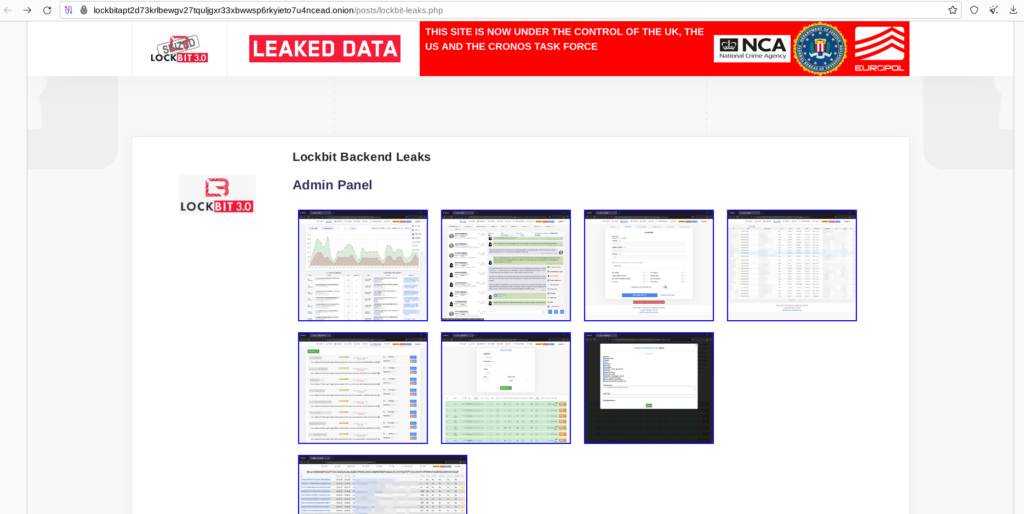
A data leak regarding the ransomware gang was also shared on the DLS, with evidence regarding the administration panel, chats, access statistics and sources of the gang’s websites.
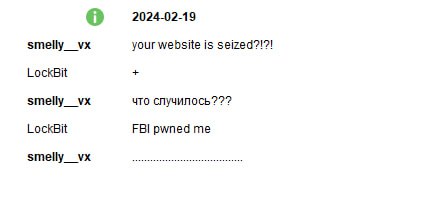
Lockbit confirmed the seizure of the assets and sent notification (the authenticity of the communication has not been verified) of the compromise to its affiliates.

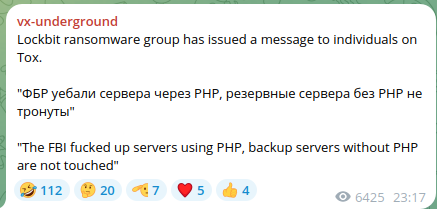
Rumors claim that the vulnerability exploited by law enforcement was CVE-2023-3824
Details regarding the police operation, which involved 10 countries and which saw the arrest of 2 people, the seizure of 200 electronic money accounts, the takedown of 23 servers, and the closure of 14,000 rogue accounts, are available at this link.







