SEC Consult researchers showed that some software allows a bad actor to inject a specially crafted email message concealing a second message hidden inside the body of the original message. This passes into the inbound SMTP server, which interprets the text as a separate second message. The attack relies on incorrect handling of the <CR><LF>.<CR><LF> sequence of the protocol of the SMTP data phase in some email servers. In this situation the attacker is able to bypass some of the SMTP origin assurance methods like SPF.
Which mail servers are vulnerable?
All those that do not comply with RFC5321 (https://www.rfc-editor.org/rfc/rfc5321#section-4.1.1.4) and RFC5322 (https://www.rfc-editor.org/rfc/rfc5322#section-2.3).
What is the most likely attack use case?
An attacker can register a free account with an email provider that uses a mail server vulnerable to SMTP smuggling to impersonate any user (for example admin@providername or support@providername) of that provider.
How can I check if my mail server is vulnerable?
You can use the script found here.
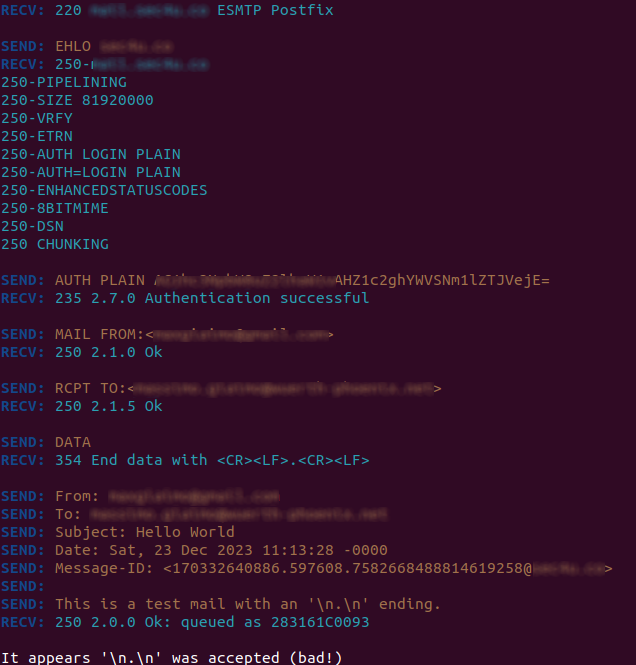
Is Exchange Online vulnerable to SMTP Smuggling?
No, the vulnerability in Exchange Online was fixed in mid-October 2023.
Is Postfix vulnerable to SMTP Smuggling?
The Postfix developers have released a patch (https://www.postfix.org/smtp-smuggling.html).
Is Sendmail vulnerable to SMTP Smuggling?
Yes, at the time of writing the Sendmail developers have not yet released a patch.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







