The Exploit Prediction Scoring System (EPSS) is a data-driven effort for estimating the likelihood (probability) that a software vulnerability will be exploited in the wild , as my colleague Beatrice Dall’Omo has already had the opportunity to talk about in this article.
EPSS was developed by FIRST (https://www.first.org/epss/) with the aim of assisting those responsible for securing organizational infrastructure to correctly prioritize the implementation of identified vulnerability remediations.
EPSS produces a probability of exploitation activity (a value between 0 and 1) over the next 30 days, and EPSS scores are currently generated daily.
During a Vulnerability Assessment activity, normally for identified vulnerabilities, a CVSS Base Score (https://www.first.org/cvss/) is assigned which evaluates the severity of a given vulnerability, applying metrics which include, for example, the vector of attack, the complexity of the attack, the privileges required to exploit the vulnerability, the interaction required on the victim’s side, the impact on scope, confidentiality, integrity and availability. However, this evaluation does not take into consideration the actual exploitation of the vulnerability for which the CVSS Base Score is calculated, as it does not use real contextual data.
EPSS tries to respond precisely to this methodological gap, adding an import list of context information to the vulnerability:
- Vendor (CPE, via NVD)
- Age of the vulnerability (Days since CVE published in MITRE CVE list)
- References with categorical labels defining their content (MITRE CVE List, NVD)
- Normalized multi-word expressions extracted from the description of the vulnerability (MITRE CVE List)
- Weakness in the vulnerability (CWE, via NVD)
- CVSS metrics (base vector from CVSS 3.x, via NVD)
- CVE is listed/discussed on a list or website (CISA KEV, Google Project Zero, Trend Micro’s Zero Day Initiative (ZDI), with more being added)
- Publicly available exploit code (Exploit-DB, GitHub, MetaSploit)
- Offense-oriented security tools and scanners: Intrigue, sn1per, jaeles, nuclei
Another fundamental source of contextual information used by EPSS is that provided by various partners, who through their in-the-wild monitoring activities manage to recover and provide information on actual attempts to exploit vulnerabilities.
We are proud to announce that we have also implemented EPSS within our Cyber Threat Intelligence Platform SATAYO. For each vulnerability identified by the platform, a query is made to the API provided by First and the calculated EPSS value is retrieved.
For example, for CVE-2016-10033, the query is made at the link https://api.first.org/data/v1/epss?cve=CVE-2023-20198&pretty=true:
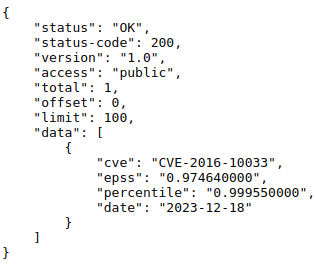
and the result within SATAYO will be as follows:
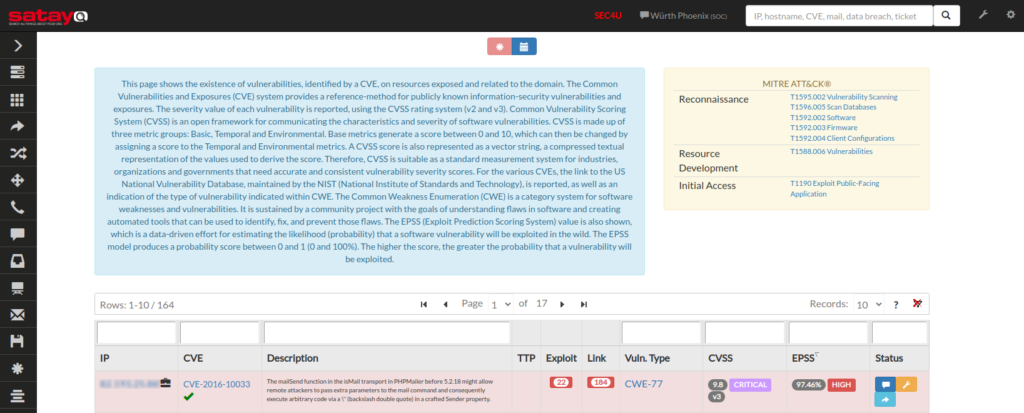
Within SATAYO we have decided to categorize vulnerabilities with EPSS between 0% and 59% as LOW, vulnerabilities with EPSS between 60% and 79% as MEDIUM, and vulnerabilities with EPSS between 80% and 100% as HIGH.
Our analysts will therefore have the availability of this additional important metric to evaluate the need to open a ticket for our customers to proceed with remediation activities.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







