There are community projects that, once implemented, become true points of reference. One of these is certainly the DRM – Dashboard Ransomware Monitor project.
This project, founded by Dario Fadda in 2020, monitors ransomware groups through scraping activities, to store claims regarding victims within a permanent RSS feed.
However not everyone knows that starting from June 2023 our SOC Attacker Centric has become an important contributor to this project. Specifically, our activity consists of enriching the data made available by the project, adding information relating to the business scope of victim organizations.
The result of this enrichment is visible within each record stored by the project.
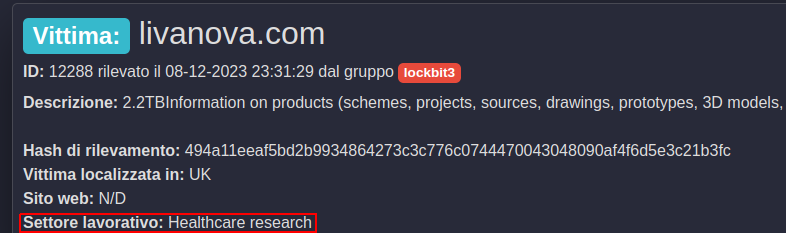
This is a task which, especially at the beginning, required a significant investment in terms of time (when we started doing the enrichment there were over 8000 records to enrich) but which today allows us to make available to the community an important piece of information that can be used as a correlation element.
In technical terms, every 4 hours we retrieve the records through the RSS made available by the project. From there, through a screen present within our SATAYO Threat Intelligence Platform, the analysts of our SOC Attacker Centric are able to carry out the enrichment of the records, choosing a specific business area from a list of over 100 sectors.
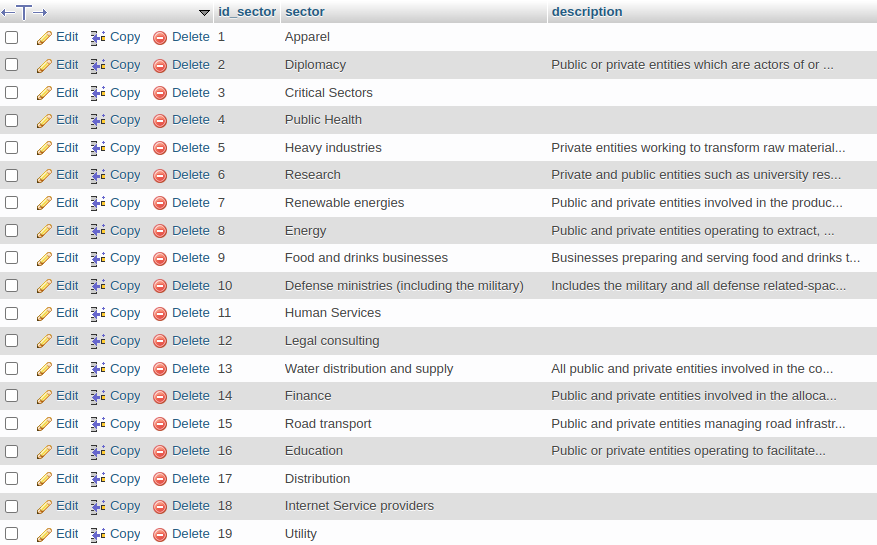
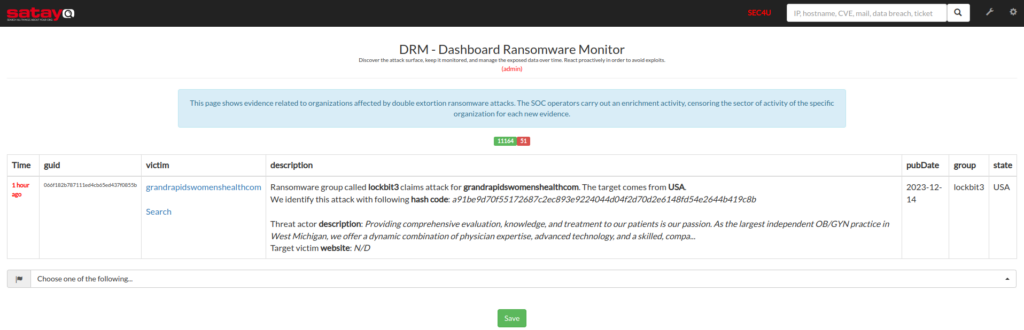
Once the enrichment is finished, we generate a .json file that we make available to the project within a web service.
This activity is carried out 24/7 by our SOC, so that a few hours after the claim by the ransomware group, the information relating to the business scope is already available.
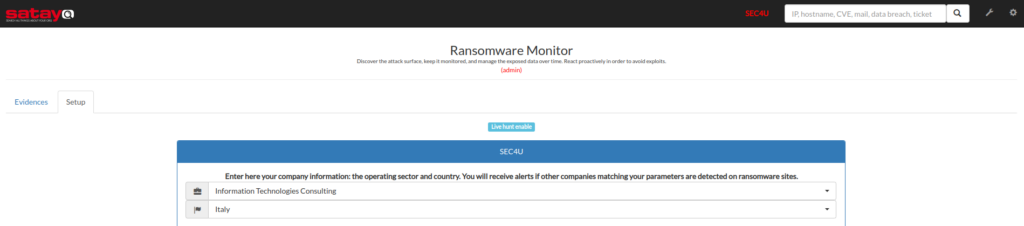
This is what we do, for example, within our SATAYO Threat Intelligence Platform, where we can register, for each monitored organization, the reference country and the business scope, in order to notify the customer of any claims relating to the organization that are in the same country or the same business area.