During a Vulnerability Remediation process, understanding which vulnerabilities pose a real and significant risk for an organization is not so obvious, and most of the time it involves several different aspects. It takes into consideration several factors related to available resources and time, company assets, severity, compatibility with fix methodologies, and others.
There is no single prioritization strategy, but companies need to define one since they typically have limited time and resources to invest in patching vulnerabilities. Thus as the Cyber security team at Würth Phoenix, we guide our customers in the initial phase of defining a remediation strategy.
After performing activities such as a Vulnerability Assessment (i.e., VA), a Vulnerability Assessment and Penetration Test (i.e., VAPT), or a Web Application Penetration Test (i.e., WAPT) on a customer perimeter, we deliver them a detailed report presenting the methodology used, the activities performed, a general remediation plan and all the vulnerabilities detected.
Then, for each vulnerability, we indicate the value of the EPSS (we’ll see later what that is) in addition to the severity based on the CVSS score, the description, some references, a proof of concept and the involved vulnerable targets. Based on the EPSS value, we also indicate the priority of each finding in the reports giving companies a measure of how important it is to fix that particular vulnerability.
In the following paragraphs, I’ll delve into the concept of the EPSS model to understand why it’s such a meaningful number to take into consideration in a Vulnerability Remediation process.
Community-driven and Data-driven Model
According to FIRST, only a small subset (around 2%-7%) of published vulnerabilities are ever seen exploited in the wild. Businesses both cannot and do not need to fix all the vulnerabilities immediately reported. This is where a good prioritization strategy and the value of EPSS comes into play, to limit the possibility of exposing companies to cyber attacks.
The Exploit Prediction Scoring System (EPSS) is an emerging standard developed by a volunteer group of researchers, academics and government personnel. It consists of a community-driven and data-driven effort that, by collecting and analyzing publicly available data, estimates the likelihood that a vulnerability will be exploited in the next 30 days. Then the model outputs a probability score between 0 and 1 (0% and 100%) where the higher the score, the greater the probability that a vulnerability will be exploited.
Currently the EPSS is collecting data from multiple sources listed below:
- MITRE’s CVE List
- “Tags” derived from the CVE description and other sources
- How many days the CVE has been published
- How many references are listed in the CVE
- Published Exploit code in Metasploit, ExploitDB and Github
- Security Scanners: Jaeles, Intrigue, Nuclei and sn1per
- CVSS v3 vectors (according to the National Vulnerability Database)
- CPE (vendor) information as published in National Vulnerability Database
- Daily observations of exploitation in the wild activity from AlienVault and Fortinet
From this, we can understand how the database of EPSS values is continuously updated and the value for a given CVE may differ from day to day.
How to Get the EPSS Value
To date, the EPSS value can be retrieved in two ways. First, you can download the CSV file from the data and statistics page and directly query it to speed up performance (remember to periodically download the CSV file so you have an updated version of the EPSS values). Second, you can simply make a request to the existing API indicating the CVE:
https://api.first.org/data/v1/epss?cve=<CVE-xxxx-xxxxx>&pretty=true
For example, by requesting the resource:
https://api.first.org/data/v1/epss?cve=CVE-1990-0497&pretty=true
the output you obtain is:
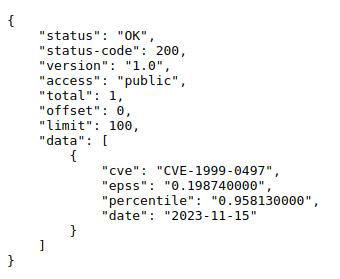
Here we see that the vulnerability CVE-1990-0497 has an EPSS of 19.87%, meaning that it’s not a priority to fix it immediately.
Using the second methodology, our Red Team has automated the process of requesting the EPSS value using the existing API for each vulnerability found during VA, VAPT or WAPT activity. Then, we automatically parse the output to extract the EPSS value and put it in the report as a percentage. Where the EPSS is more than 80%, the priority for that vulnerability is high, while if the EPSS is between 50% and 80% the priority is medium, and finally if the EPSS is less than 50% the priority is low. Below is an example of how the EPSS value is shown in our VA, VAPT or WAPT reports, for each vulnerability found.
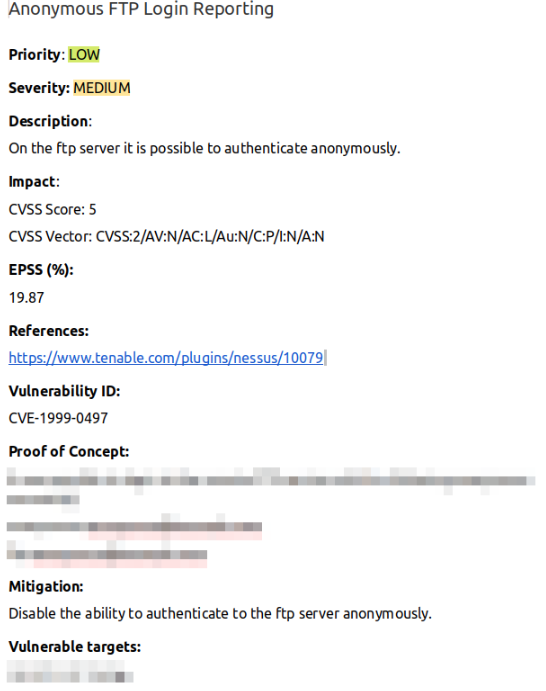
For privacy reasons, the Proof of Concept and the vulnerable targets fields have been blurred out.
Since it’s only possible to calculate the EPSS value for published CVEs, if a CVE is ever issued for a given vulnerability, then for priority we’ll report the value as HIGH / MEDIUM / LOW based on the CVSS score.
Conclusion
Remember that the EPSS is a statistical value that will improve over time given the huge amount of vulnerability and exploit data available these days. While it doesn’t replace human analysis, it does help businesses (and others as well) in prioritizing vulnerabilities via automation without tipping the absolute decision-making balance by itself. Providing the EPSS values together with each vulnerability detected allows our customers to get an overview about the short and long term actions to carry out after we perform offensive activities (i.e., VA, VAPT and WAPT) on their infrastructures or assets.
For more information have a look to our services here, or contact us directly !
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







