The daily monitoring activities that we carry out within our Security Operation Center Attacker Centric have allowed us to identify the spread of a new infostealer type malware.
Log (or information) stealer malware is a type of Trojan that gathers data in order to send it to the attacker. Typical targets are credentials saved in browser profiles.
Examples of this type of malware are the well-known Redline, Raccoon, Vidar, Metastealer, Eternity, and Prynt.
The latest malware infostealer is called Risepro, and the evidence collected through its use is already up to more than 2200 within the Russian Market market place. The first evidence was published on the market on 9 December 2022 by the seller Mo####yf.
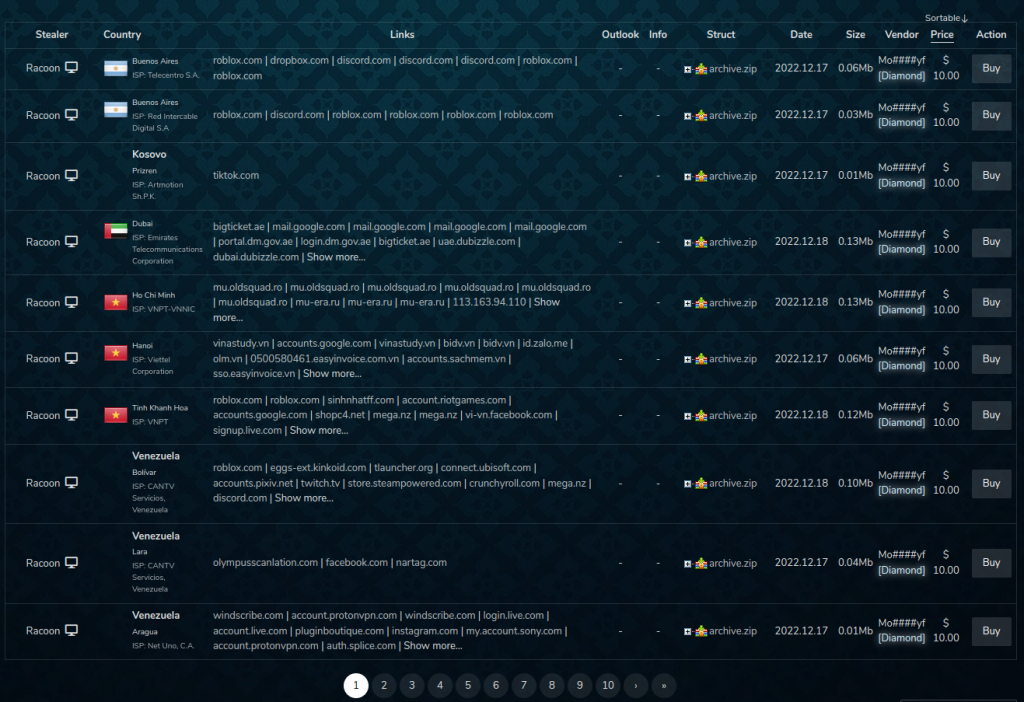
Record related to Risepro activities
After obtaining one of the records we were able to carry out further analyses related to the malware. The structure visible within the record is very similar to the structure made available within records originating from the activity of other infostealers.
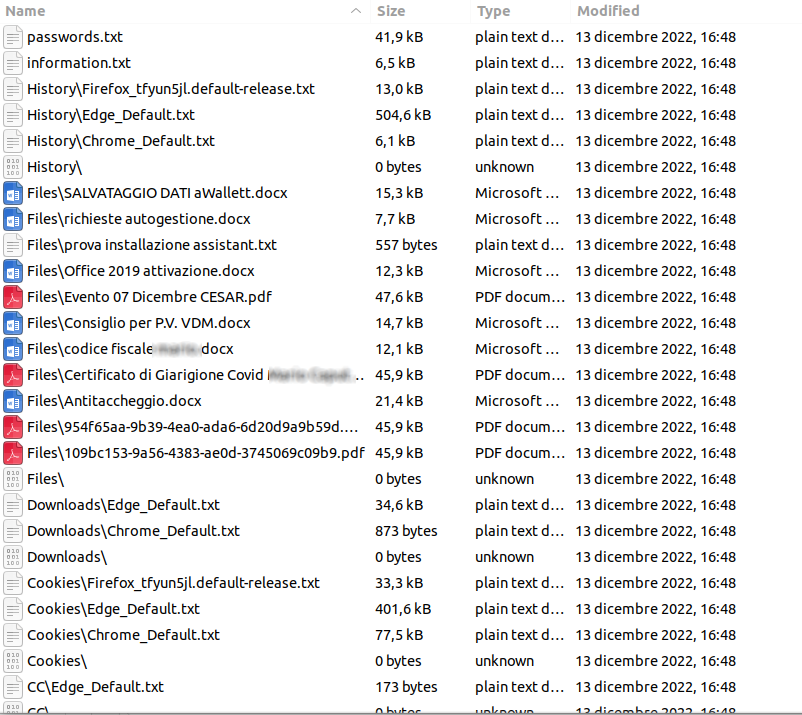
Inside the passwords.txt file it’s possible to obtain information about the Telegram user of the owner of the malware.
Also related to Risepro is a trace in Telegram of a bot that currently does not provide any particular information apart from its Telegram ID.
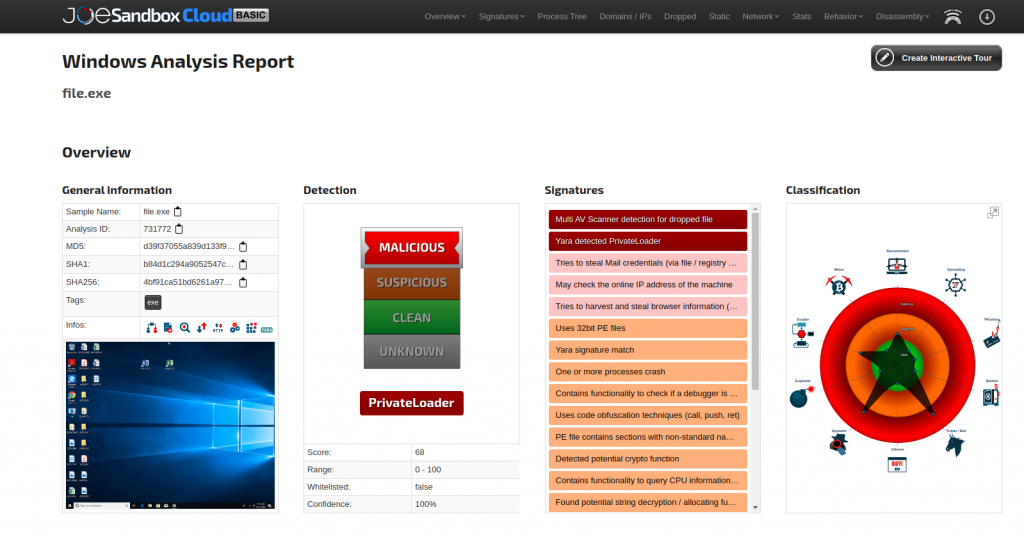
Additional information regarding the malware has been identified within the Joe Sandbox at https://www.joesandbox.com/analysis/731772/1/html. The most useful information concerned the MD5 hash of the malware and the IP of the command & control (C2) server.
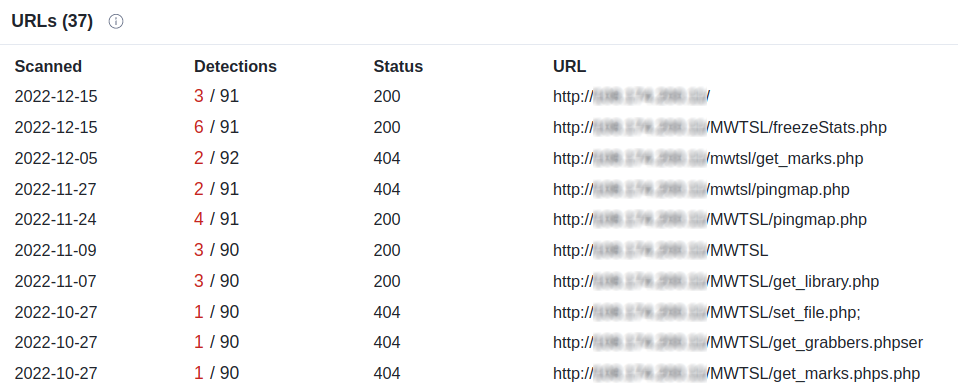
The IP of the C2 server is listening on HTTP port 80 and shows the following file and directory structure:
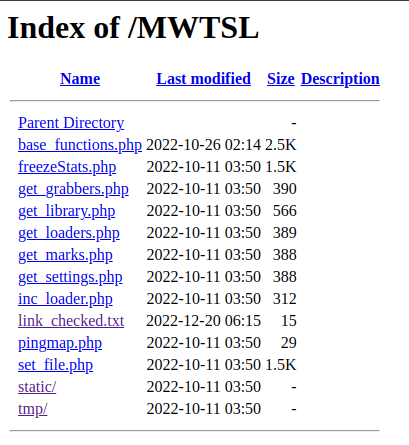
The link_checked.txt file is apparently used by the agent to contact the C2 server.
A search of the hash of the malware on Virustotal Enterprise allowed us to verify the level of detection of the malware, detected by most of the engines. The first malware submission to Virustotal was done on 2022-10-28 12:42:40 UTC.
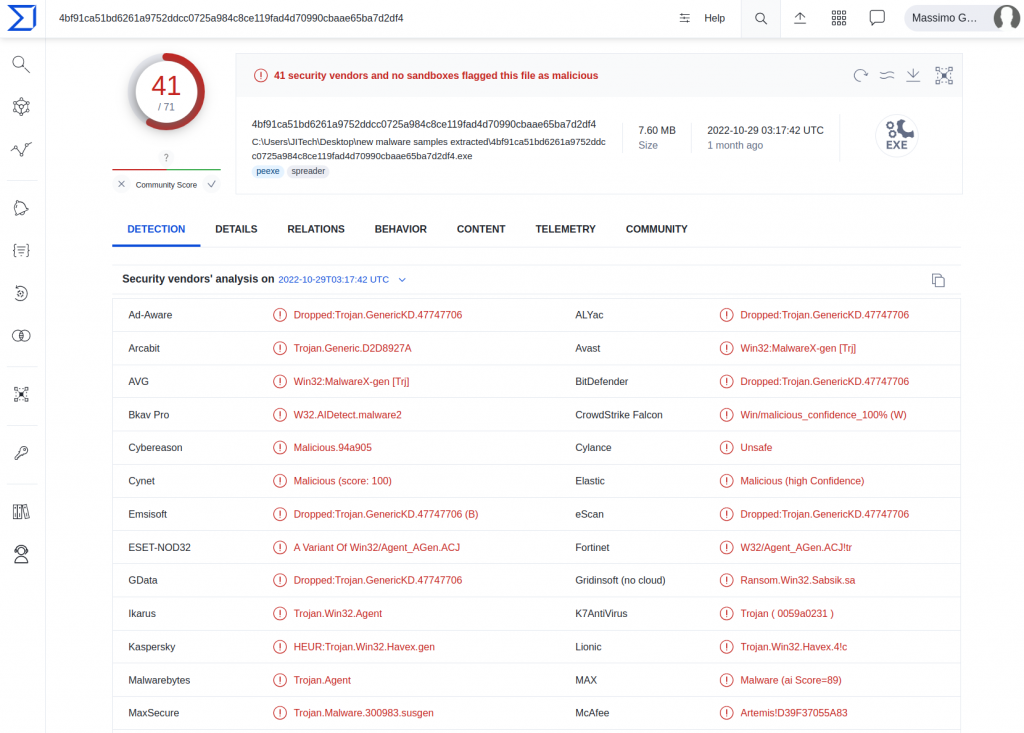
Virustotal’s detection also provides tangible information on the C2 server’s IP.
At the moment the apparent owner of the malware does not appear to have shared information within well-known forums such as XSS, BHF and Exploit.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find security issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







