A Look Inside Dark Angels Negotiation and Some Details about Their TTP
Starting from a static analysis done by Cyble Research Lab (https://blog.cyble.com/2022/05/06/rebranded-babuk-ransomware-in-action-darkangels-ransomware-performs-targeted-attack/) of ransomware called Dark Angels, we gained evidence about the activities of the Dark Angels ransomware group.
An OSINT analysis carried out by our Würth Phoenix team helped to reach the Ransom Operator blog and one of the victim pages.
Based on the evidence gathered, it seems that the approach of the Dark Angels operators tends to create a single page for each victim, accessible from a unique URL.
The homepage displays a simple page with a logo without any information about the ransomware group or its victims.

The hidden service is poorly configured and some misconfigurations permitted us to understand details about the infrastructure used by this threat actor.
The application was published only on the HTTPS protocol and it exposes a self-signed certificate.
The whole site was developed using Symfony PHP framework. Metadata of the exposed files display a 2020 date. The hidden service could be an old project deployed for a targeted attack.
In the header of the victim page there is a countdown. In the body of the page there are multiple pieces of evidence regarding the exfiltrated materials. The group doesn’t use a CDN, every file shared on the victim page is distributed using the ufile[.]io sharing service.

Further analysis of the page used to publish the victim’s details pointed us to the chat section used by cybercriminals to conduct the negotiation phase.
In the negotiations, when the victim asked what they could do to recover the encrypted files, the cybercriminals first asked for about 8 million dollars and afterwards lowered the amount of the request to 1.5 million.
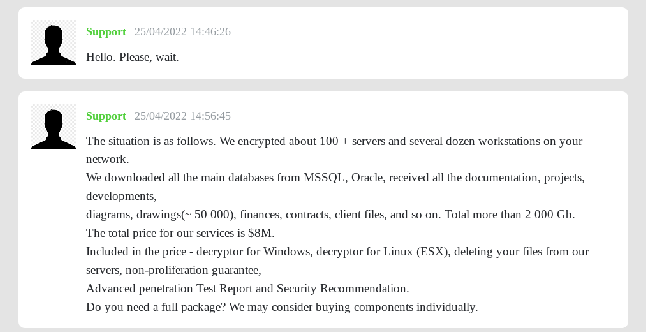
It’s a relevant fact that the cybercriminals evaluated the victim’s revenue and the insurance trade in general before continuing the deal. Based on what the chat exposes, they reached an agreement where the cybercriminals offered decryptors for both Windows and ESXI servers, backups of the files they exfiltrated and a full write-up about how they conducted the attack.
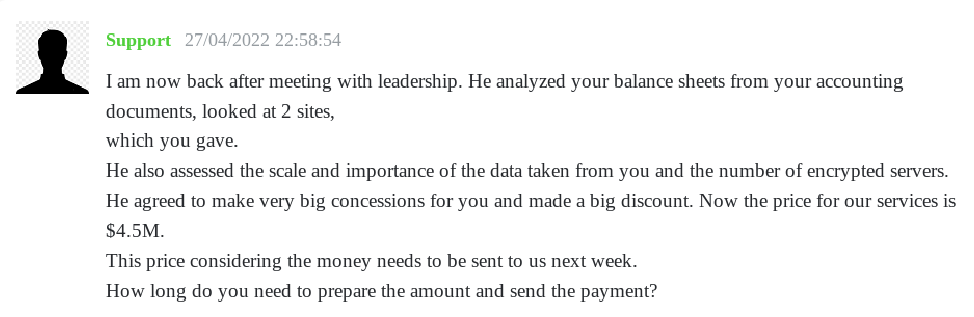
The cybercriminals shared a Bitcoin address used to received the payment. They received the sum of 38BTC which was split with 2 new address some minutes later.
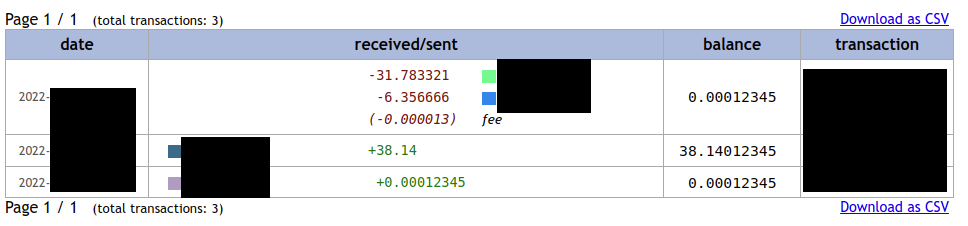
The full chat history is a treasure trove of information which can help us understand how this cybergang works. The cybercriminals used the chat section of the site to distribute sensitive information.
The chat contains links for data like full backup, password, decryptor and BTC addresses used during the negotiation. Reading the full write-up shared by the ransomware operator helped us to understand their TTP.
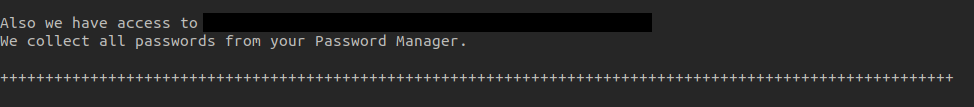
A more detailed version of the document was also shared. This report contained credentials and details about each compromised machine. They explained that the company’s password manager company was also breached and they got all the passwords it contained.
After the conclusion of the deal, the operators published an archive containing logs of the removal of data. The archive contained 4 log files in raw .txt with the output obtained by Powershell scripts and the Linux rm command. It’s clear that this kind of proof can be easily tampered with or crafted.
Based on the reports they shared, the cybercriminals obtained a first footprint in the victim’s perimeter using malspam. They used a RAT to gain access to the first machine. After that, they opened a SOCK5 backdoor to maintain access to the compromised machine.
In the next stage they scanned the network in order to obtain access to older machines. They obtained access to an old Window Server 2012 as domain admin and then they extracted the ntds.dit using vssadmin.
The next step involved cracking hashes obtained from that file and retrieving other valid credentials.
From there they moved laterally and obtained access to some NAS instances and other enterprise assets. Based on what they wrote in their report, weak and common passwords helped them to reach a deep level of compromise.
In the following step they started to gather sensitive data, then they exfiltrated whatever could be used to reinforce the negotiation phase. The attack ended by opening an ssh connection on an ESXI server and encrypting virtual machines using the ESXI version of the ransomware.
The operations lasted 11 hours and the ransomware team obtained access to the perimeter 5 months before the encryption phase.
In the document, as a real pentest, the operators also offered advice on avoiding future incidents. They suggested methodologies and products to mitigate further ransomware attacks.
MITRE MATRIX
TA00043: Reconnaissance
T1589: Gather Victim Identity Information
T1590: Gather Victim Network Information
TA0001: Initial Access
T1566: Phishing
T1078: Valid Accounts
TA0006: Credential Access
T1110: Brute Force
T1555: Credentials from Password Stores
T1003: OS Credential Dumping
T1552: Unsecured Credentials
TA0002: Execution
T1047: Windows Management Instrumentation
TA0003: Persistence
T1505: Server Software Component
T1078: Valid Accounts
TA0004: Privilege Escalation
T1068: Exploitation for Privilege Escalation
T1078: Valid Accounts
TA0005: Defense Evasion
T1078: Valid Accounts
TA0006: Credential Access
T1110: Brute Force
T1555: Credentials from Password Stores
T1003: OS Credential Dumping
T1552: Unsecured Credentials
TA0007: Discovery
T1087: Account Discovery
T1083: File and Directory Discovery
T1135: Network Share Discovery
T1018: Remote System Discovery
T1518: Software Discovery
T1016: System Network Configuration Discovery
T1033: System Owner/User Discovery
TA0008: Lateral Movement
T1021: Remote Services
TA0009: Collection
T1005: Data from Local System
T1039: Data from Network Shared Drive
TA0010: Exfiltration
T1011: Exfiltration Over Other Network Medium
T1537: Transfer Data to Cloud Account
TA0040: Impact
T1485: Data Destruction
T1486: Data Encrypted for Impact
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find security issues interesting, maybe you could start in a roles like this as well as other roles here at Würth Phoenix.







