Within our Attacker Centric Security Operation Center, we look for the best detection rules every day to help you detect attack scenarios.
One of the most important projects that we use as a source in this area is without doubt that of Sigma Rule (https://github.com/SigmaHQ/sigma).
The project, founded by Florian Roth (https://www.linkedin.com/in/floroth/), has almost 300 contributors and has been an international reference point for years.
Sigma is a generic and open signature format that allows you to describe relevant log events in a straightforward manner. The rule format is very flexible, easy to write and applicable to any type of log file. The main purpose of this project is to provide a structured form in which researchers or analysts can describe their once developed detection methods and make them shareable with others.
But how can you get a complete list of the Sigma Rules present in the GitHub repository, so that you can easily search for and activate only those related to the technologies present in your infrastructure?
Starting today you can have this list thanks to a tool that I developed within the SEC4U team at Würth Phoenix.
In our team we’re always very eager to share with the community what we discover and think are interesting, and we’ve therefore decided to make the results of this tool available to everyone. You can find it at the link https://github.com/SimoneCagol/sigma-rules-crawler.
From a technical point of view, the tool connects to the page https://github.com/SigmaHQ/sigma/blob/master/rules and checks all the rules present, extracting the following fields from each:
- Title
- Description
- Path
- Date
- Link to download the rule
The tool then loads the results into the GitHub project, using the APIs made available by the platform.
Here’s what running the tool looks like:
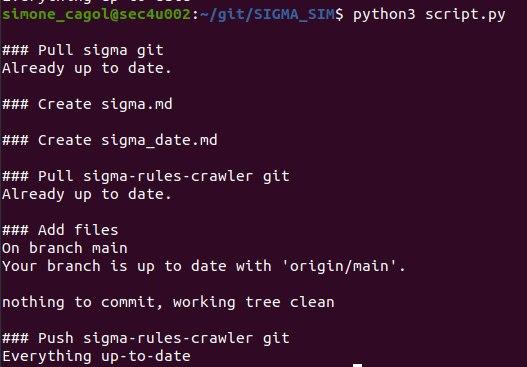
And this is the final result within the GitHub project:
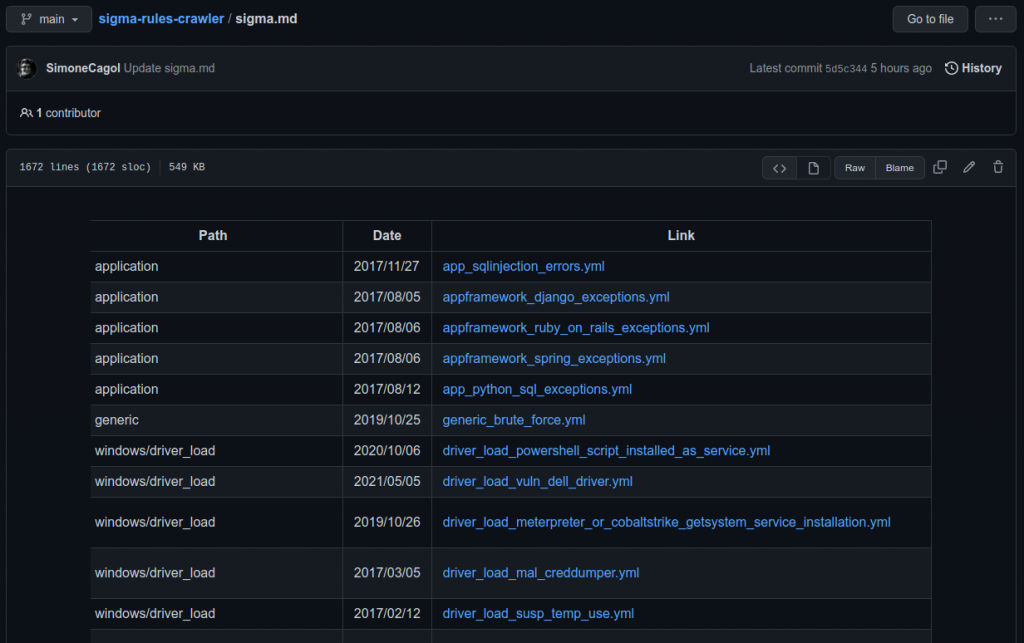
Two files are loaded on the project: one presents the complete list of rules, while the other presents the full list of rules ordered by commit date.
The tool is configured to run several times a day within a host present in our cloud, and can thus maintain a continuously updated list.






