Microsoft Exchange 0-Day: Let’s Look at the Facts!
I’m writing this article with the goal of summarizing the events of recent days concerning the zero-day vulnerability that has struck Microsoft Exchange installations, and to provide some useful information to help you understand how the attack began, how it developed, and what we should expect in the immediate future.
First of all, a quick explanation is in order of what a zero-day exploit is: we’re talking about a vulnerability that the developer or software company was unaware of on the day the vulnerability notice was publicly released. This means that at that moment no patch is available, and that the only hope for defending yourself from being exploited by attacks against that vulnerability lie in additional layers of security (which is why the concept of security in depth is so vitally important). For instance, you should inspect your perimeter firewalls, Web Application Firewalls (WAFs), Intrusion Detection Systems, Endpoint Detection and Response, and others.
How extensive is the problem?
Or rather, what attack surface might attackers take advantage of? If we use Shodan (https://shodan.io) to find out how many Microsoft Exchange 2013 and 2016 installations are exposed on the web, we get about 237K results (using the search string ”X-AspNet-Version http.title:”Outlook” –”x-owa-version”
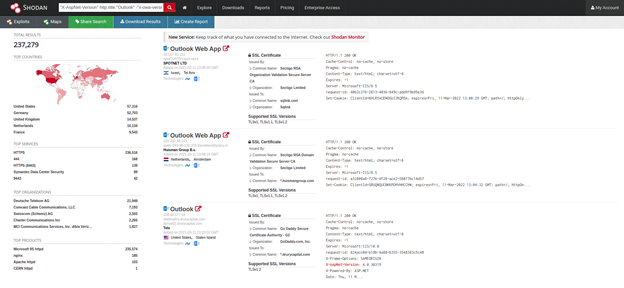
But we also get 177 results for Exchange 2010 ("x-owa-version" "IE=EmulateIE7" http.favicon.hash:442749392) with End of Support on October 13th, 2010, and (I’m not kidding here) 479 results for Exchange 2007 ("x-owa-version" "IE=EmulateIE7" "Server: Microsoft-IIS/7.0") whose support ended April 11th, 2011.
Exactly which vulnerabilities are we talking about?
Or specifically, which vulnerabilities are those that allowed cyberattackers to penetrate a very impressive number of servers recently: 30K organizations in the United States alone according to security researcher Brian Krebs?
We’re talking about 4 distinct CVEs here:
CVE-2021-26855 (CVSS:3.0 9.1)
CVE-2021-26857 (CVSS:3.0 7.8)
CVE-2021-26858 (CVSS:3.0 7.8)
CVE-2021-27065 (CVSS:3.0 7.8)
What do we know about the attack?
The Cyber Security Analysts at FireEye had already in the early days of 2021 discovered active exploits of this vulnerability (related to CVE-2021-26855 and CVE-2021-26858) and later on verified that one of the first activities of attackers was positioning a web shell on target systems. The web shell matched the signature of the famous China Chopper.
The presence of this shell implies the attack is the work of the Chinese group HAFNIUM, which historically has worked against targets in the USA by basing them off of VPS’s (virtual private servers) residing within the borders of the USA itself. In some situations, researchers have noted that the attackers executed a command to attempt to remove the administrator user from the group Exchange Organizations administrators.
Later post-exploitation activities were identified by Microsoft as the following:
- Theft of credentials via memory dump of the LSASS process (an attack technique well-documented within the Mitre Attack project)
- Compressing data using 7-Zip for exfiltration at a later date
- Utilizing Exchange PowerShell Snap-ins to export mailboxes
- Use of additional security tools like Covenant, Nishang and PowerCat for remote access
In general, post-exploitation behaviors are well described by Microsoft at this link.
Another excellent attack analysis, with an indication of the TTP (Tactics, Techniques and Procedures) used is available here.
A Sigma Rule (https://github.com/SigmaHQ/sigma/blob/master/rules/web/web_exchange_exploitation_hafnium.yml) has also been available for several days now. It can be imported into NetEye SIEM to carry out the detection of exploit attempts.
Finally, a Proof of Concept of the CVE-2021-26855 exploit has recently been published in a GitHub repository.
What can I do to check if my own server has been penetrated?
My first advice is to look inside the following paths:C:\inetpub\wwwroot\aspnet_client\
C:\inetpub\wwwroot\aspnet_client\system_web\%PROGRAMFILES%\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\
C:\Exchange\FrontEnd\HttpProxy\owa\auth
You should check for the presence of the China Chopper shell used by the attackers. An updated list of how this shell file may appear is available at this link.
If this shell is present, it means that the server has certainly already been compromised, and it’s thus necessary to go into “Incident Management” mode.
Microsoft has released several tools that allow you to investigate your own Exchange server to verify whether or not it has been compromised. These tools look for Indicators of Compromise (IoCs) that have been collected recently, such as certain IP addresses, domains, shell names, and file hashes.
What’s absolutely necessary to do now?
If you haven’t already installed patches on your server, do it now!
Microsoft has released patches for several versions of Exchange, available here.
For anyone who cannot install the patch, Microsoft has released some mitigation alternatives.
Concerning the indicators of compromise above, in particular the IP addresses used by the attackers, an excellent source of information can be found here. I advise using this list of IP addresses by importing them directly into your firewall devices so you can create drop rules and/or traffic logs (as needed), and in general using other tools like SIEM as contextual data tools for your own detective work. These can also be useful for immediately checking the possible presence of connections used by the attackers to exfiltrate data.
At this link you can find an NMAP script to check if a given server is vulnerable. It works with this simple command:nmap --script http-vuln-exchange -p443 $target
What should we expect in the near term?
Certainly successful attacks will continue over the next few weeks due to the generally slow nature of administrators learning about the vulnerability and patching their systems. In addition, over the next several months the attackers, who are currently in a vigorous data collection phase, will begin to exploit any data stolen – most likely via targeted extortion strategies (certainly for the most sensitive targets they’ve already completed their hacking operations).
One of the HAFNIUM groups’ activities that surely will be put into practice will be searching for interesting information within the dumps recovered from the LSASS processes, and above all whatever they find inside stolen mailboxes by searching them. You can imagine how much important and interesting information we keep inside our mailboxes: telephone numbers, private conversations and attachments, authentication credentials, passwordless authentication keys, appointments, etc. My advice is to do these same searches yourself (starting with a simple keyword search for “password” before trying out more wild ideas), and anticipate the moves of your attackers, who already have quite an advantage on you.
How can we keep up-to-date on this situation?
A number of information channels are kept constantly updated. The most important of these are certainly through the national CSIRTs (Computer Security Incident Response Team):
In Italy, CSIRT Italy has created a dedicated and frequently updated page: https://csirt.gov.it/exchange
In Germany, Bundesamt für Sicherheit in der Informationstechnik has published a document here: https://www.bsi.bund.de/SharedDocs/Cybersicherheitswarnungen/DE/2021/2021-197772-1132.pdf?__blob=publicationFile&v=16
In the UK there is advice by the National Cyber Security Centre https://www.ncsc.gov.uk/news/advice-following-microsoft-vulnerabilities-exploitation
Spain has the page of the Centro Criptológico Nacional, at the link https://www.ccn-cert.cni.es/seguridad-al-dia/avisos-ccn-cert/10892-ccn-cert-av-12-21-vulnerabilidades-en-microsoft.html
Other notices from national CSIRT organizations are as follows:
Austria: https://cert.at/de/warnungen/…
Switzerland: https://www.govcert.admin.ch/…
Netherlands: https://www.ncsc.nl/…
France: https://www.cert.ssi.gouv.fr/…
United States: https://us-cert.cisa.gov/…
Canada: https://www.cyber.gc.ca/…







