In order to protect your business against cyber attacks you need to both harden your systems and promptly detect suspicious activities in your infrastructure.
Sigma is an open source project which defines specifications for a standard signature format that allows you to describe relevant log events for security purposes. The Sigma rules language is intended to be flexible and straightforward, and can be converted using Sigma Converter (also called sigmac) into queries for many different targets such as Elasticsearch, Qradar, Splunk etc.

Alongside its language definition and converter, the Sigma project also provides hundreds of attack signatures developed by the community to detect cyber attacks and vulnerabilities such as brute force attacks, clear-text protocol usage, permission changes, usage of suspicious programs such as Mimikatz, and others.
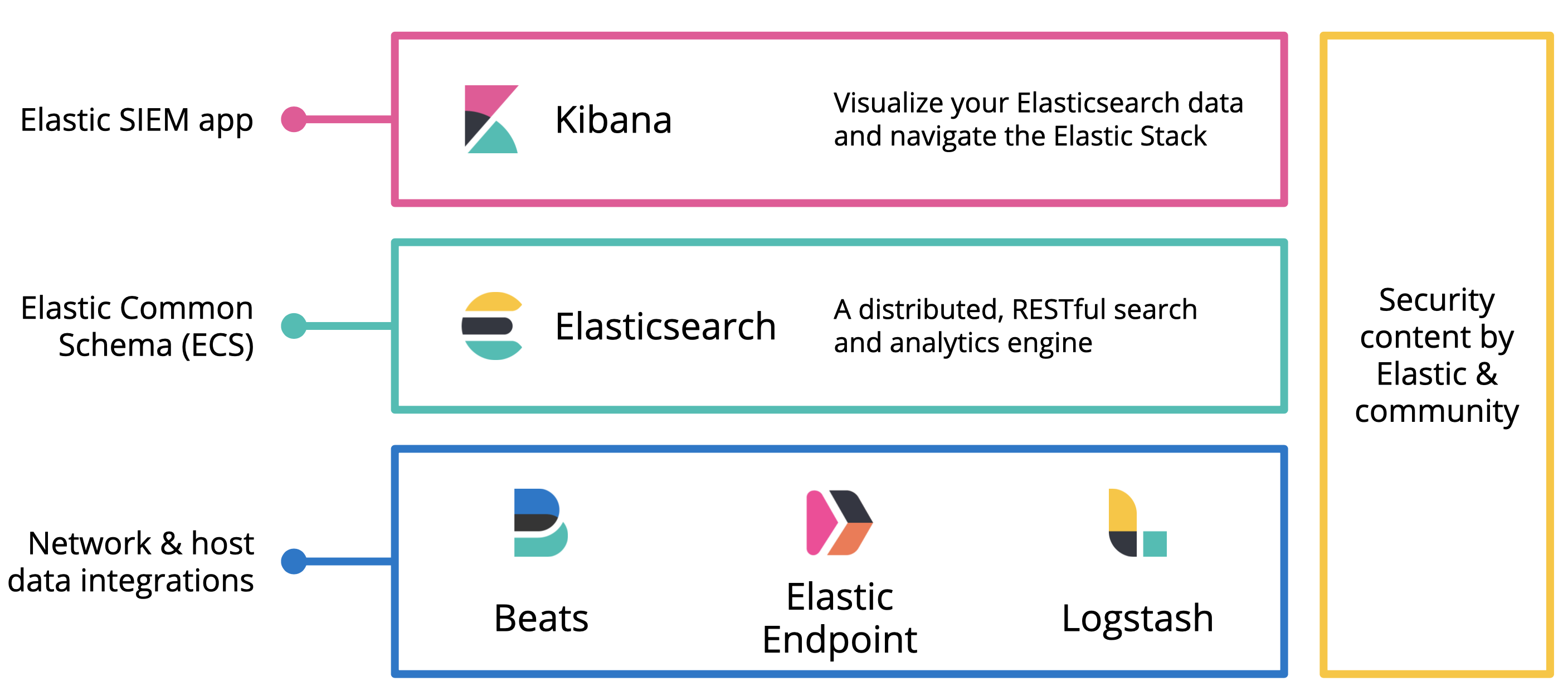
NetEye SIEM provides a set of powerful tools based on Elasticsearch SIEM to collect and analyze logs from different sources. SIEM was introduced with Elastic 7.5, and one of its most interesting feature is the detection engine rules: it provides methods to automatically detect suspicious activity across your infrastructure. When a rule is triggered, a signal is created. You can then use the Kibana SIEM dashboard to visualize the generated signal.
Sigmac does not support the new detection feature by default; however, it is possible to convert sigma rules into valid detections. To achieve this, we have developed a dedicated sigma config file for NetEye 4 alongside a tool to convert xpack-watchers produced by sigmac into detection.
Thanks to these tools, hundreds of sigma rules can be imported into NetEye SIEM and used to protect your infrastructure from cyber attacks.
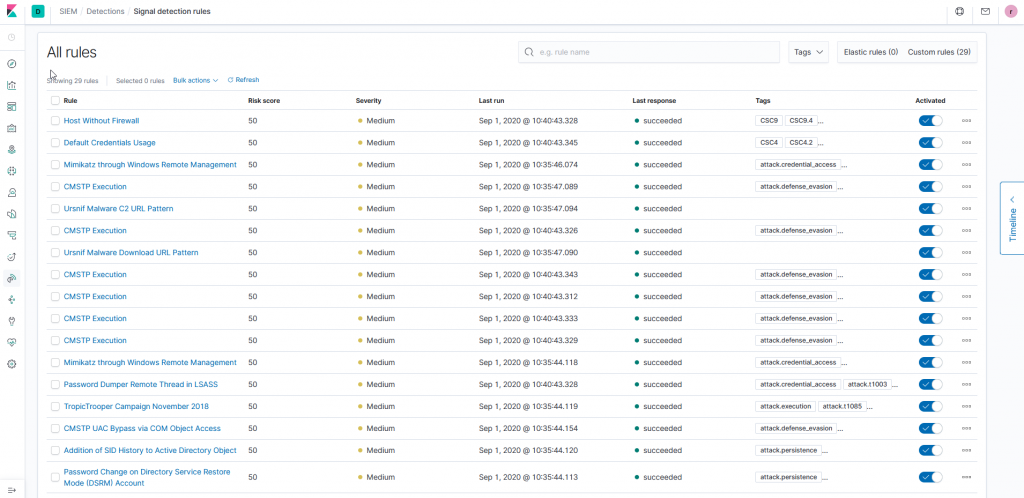
In the example below, the rule User Added to Local Administrators has been converted and imported to scan logs collected in NetEye: it detects a user promoted to local administrator on a host monitored using Winlogbeat.
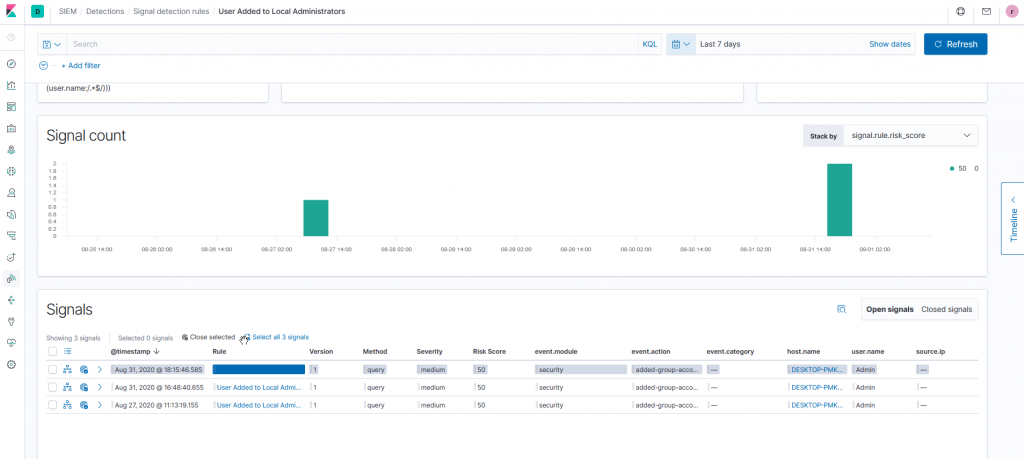
When a signal is generated, a notification can be sent through the Kibana Alerting and Actions framework, or through NetEye.







