Customizing the Default Permissions in NetEye SIEM
Starting from NetEye 4.12, NetEye SIEM is secured with X-Pack Security. NetEye comes pre-configured with some users and roles (see NetEye User Guide > Log Manager > Elasticsearch Access Control) to grant the Elastic Stack the ability to ingest, manage, and view the logs that you want to collect.
For example, NetEye provides:
- A Kibana administrator to manage all the permissions, logs, and configurations within the Elastic Stack
- A Tornado user to allow Tornado to write into the Elasticsearch indices
- And much more
But… it’s possible that the permissions provided for a particular user aren’t sufficient. If you’re going to change the pre-configuration provided in NetEye, you may lose them after an upgrade or even with an update.
So the question is: how can I safely extend the permissions of a particular pre-configured user?
The answer is to use role mapping.
Let’s suppose you want to extend the Tornado user permissions to gain full control of a new Elasticsearch index called “my-tornado-index”. The role is the following:
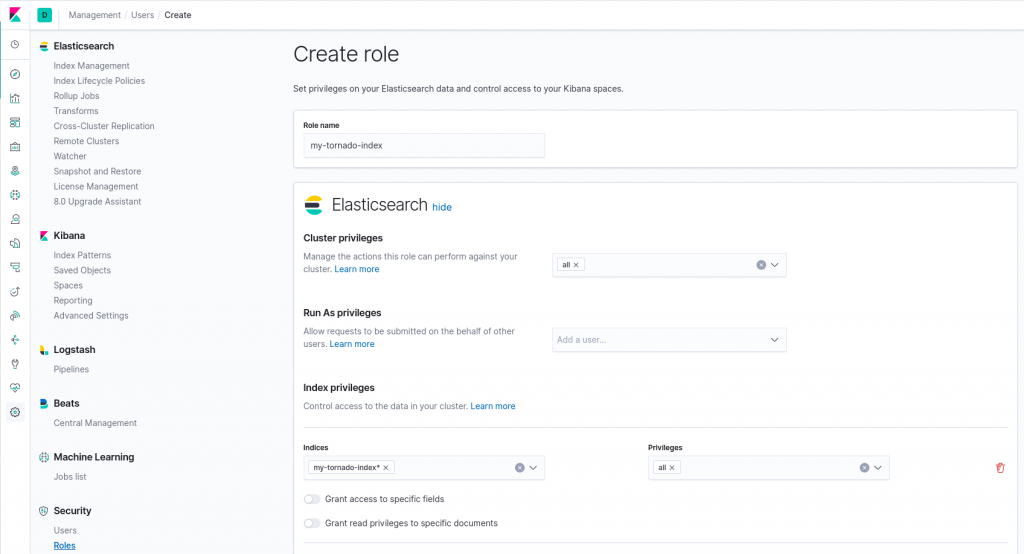
Now let’s create the role mapping that will map the aforementioned role to my user tornado:
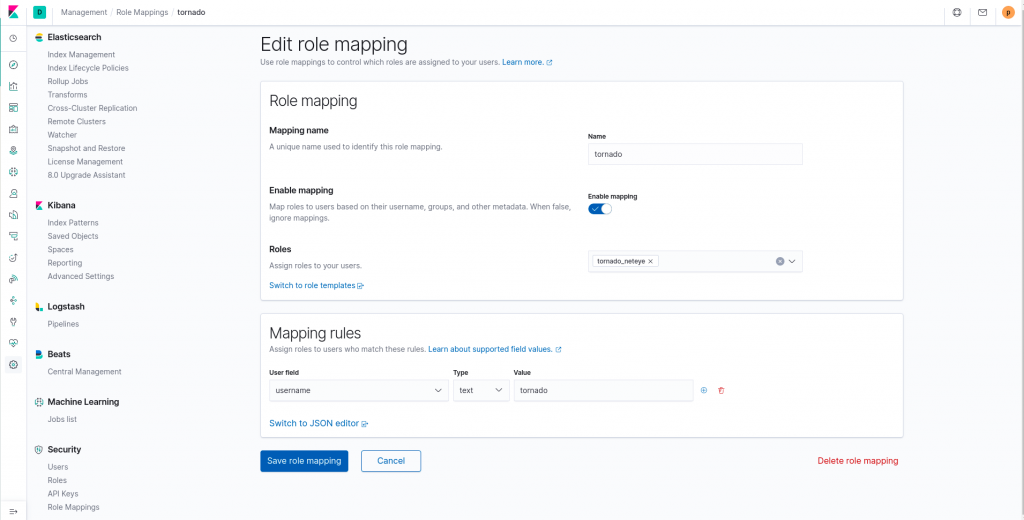
These role mappings will not be changed in future NetEye releases, and so it’s a safe way to customize the permissions of users created by default.







