NetEye as essential component of a Security Operations Centers
During my last projects I noticed that the implementation of a „Security Operations Center“ (in short SOC) is becoming increasingly important, especially for our enterprise customers.
Mainly for big companies that are of public interest like banks, energy providers, assurances etc. the topic of cyber threats is getting more actual and requires special attention. This has been reinforced not at least by the fact that some of these companies already have felt victim to cyber-attacks.
Many companies are planning to introduce a Security Operations Center to prevent and combat cyber threats. (Security Operations Center on Wikipedia) Certainly, such a SOC has to be adapted to the requirements of the company, however, at the same time it has to be flexible enough to face challenges like rapid growth and continuously changing requirements.
The implementation of our Unified Monitoring solution NetEye supports the successful realization of a SOC in the following areas:
- continuous monitoring
- Log Management and Anomaly Detection
- DDoS damage limitation
- Reporting
Let’s have a look at the single areas:
Continuous Monitoring
The „standard“ system monitoring, hence monitoring hardware, operating systems, services and processes (DNS, DHCP, NTP,Active Directory etc.), the collection of valuable data about resources and the measurement of system performance (CPU, RAM, load, disk usage, file size, etc.) belong to the basic functions of NetEye.
Log Management and Anomaly Detection
Since the release of NetEye 3.5 our solution contains a comprehensive Log Management module that is based on the well-known Elastic Stack. The module gathers, indexes, and aggregates events. It also enables individual searches and can react to all events automatically. (consider also this article „WÜRTHPHOENIX NetEye: Our Elastic Stack Story“)
For quite some time we have been investing also in the topic anomaly detection for smarter alert creation.
DDoS damage limitation
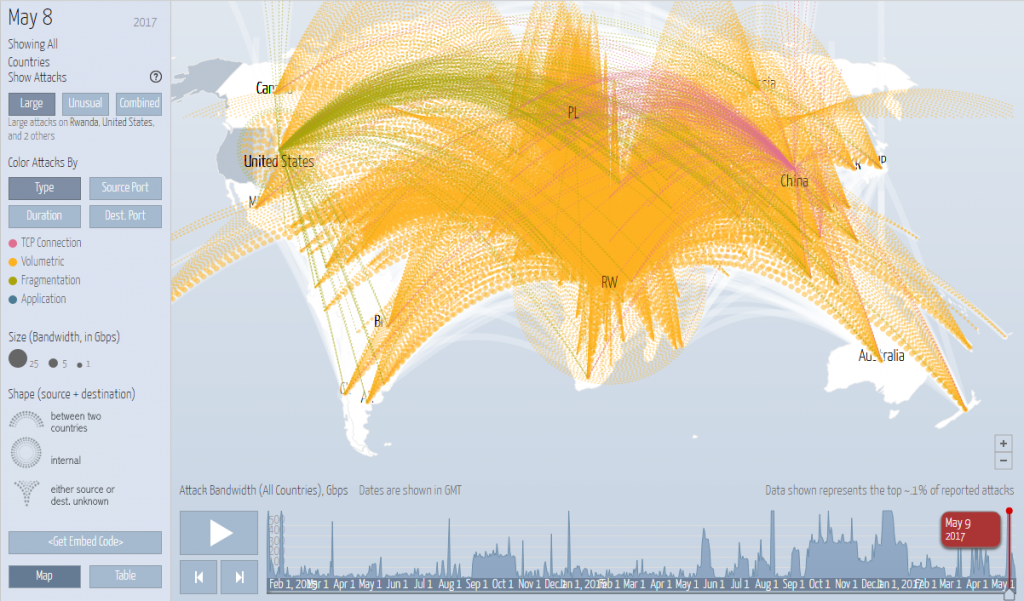
The usage of NetEye is particularly interesting to analyse data from a DDoS (Distributed Denial of Service) mitigation system. Since they tie up webservers and sometimes even entire networks DDoS attacks are one of the most common and most harmful cyber-attacks. (The most famous example is the attack of Dyn’s DNS infrastructure. See the article on theguardian.com)
The frequency of occurrence of such attacks is shown on the map below, that displays the attacks of May, 8th 2017. (The website http://www.digitalattackmap.com/ continuously provides this map).
As soon as a system is attacked, time is of the essence. Quickly recognizing the attack is crucial for reducing damages. To do so, DDoS Mitigation Systems are applied. Data (logs) collected by these systems can be sent to the NetEye Log Management. It’s efficient and central logging architecture allows:
- to pull log data from different layers on your IT infrastructure (applications, web servers, databases, firewalls)
- to parse the logs in order that they can be analyzed
- to store the logs
- to visualizes the logs on intuitive dashboards
In this way, possible attacks can be analyzed in a second moment to understand where they came from and who has caused them.
Reporting
The reporting module of NetEye enables the creation of individual reports and the scheduling of respective delivery. It further reports the predefined service level agreements and provides the possibility to automatically distribute the reports via email.
Conclusion
Cyber attacks are a real threat and should therefore not be underestimated. For larger companies the deployment of a Security Operations Center will soon become necessary. In this context, NetEye and our experienced consultants can be of great support.