Asset Management in NetEye: Management of smartphones, tablets and SIM cards
[box]
IT Asset Management (ITAM) entails collecting inventory, financial and contractual data to manage the IT asset throughout its life cycle. ITAM depends on robust processes, with tools to automate manual processes. Capturing and integrating autodiscovery/inventory, financial and contractual data in a central repository for all IT assets enables the functions to effectively manage vendors and a software and hardware asset portfolio from requisition through retirement, thus monitoring the asset’s performance throughout its life cycle.
http://www.gartner.com/it-glossary/it-asset-management-itam/
[/box]
Nowadays, reducing costs, increasing service levels and improving visibility of financial and operational decisions, has become a MUST for most IT departments.
Therefore, it is strategically important to be equipped with tools to manage the contracts related to hardware in use, software and licenses.
The aim is, being able to efficiently negotiate with suppliers, to define a targeted acquisitions strategy, to perform all updates in time, to monitor the expiration of contracts and software licenses, as well as hardware maintenance.
Asset Management in NetEye
Thanks to the integration of GLPI and OCS Inventory, NetEye provides the Inventory and Asset Management module, with which you are able to achieve the above-mentioned goals and to optimize operating costs.
The Asset Management module allows you to manage all technical resources such as computers, software, printers and peripherals, and to connect them to the related contracts, suppliers and users.
Since it became common to provide smartphones, tablets, internet sticks (and SIM cards) to its employees, most IT departments need to manage these (quickly changing) information.
With the NetEye Asset Management, it is possible to efficiently handle the following information:
- Inventory of mobile devices and contracts are natively handled in great detail
- Inventory of the SIM cards is available with a plug-in of GLPI version 0.83
Goals
The objectives that can be achieved are:
- Comprehensive Management of the mobile devices (with extensive notes and attachment of documents)
- Complete inventory management of SIM cards
- Connection of mobile devices with the relative SIM card and user
- Connection of mobile devices with the relative SIM card and supplier-contract
- History of the usage of devices, cards and contracts
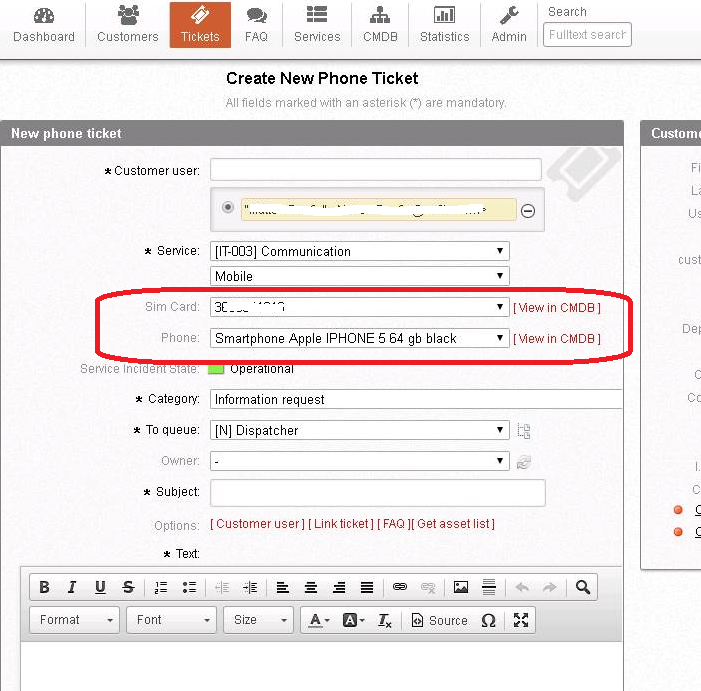
- Integration with the EriZone CMDB to show the user’s assets to the Service Desk employees and to allow the connection between ticket and asset
In addition, the asset type “SIM card” can be connected to the asset type “computer” and “device”.
By using the plugin “File Injection”, you can upload huge amounts of data regarding SIM cards, mobile devices and contracts.
Screenshots
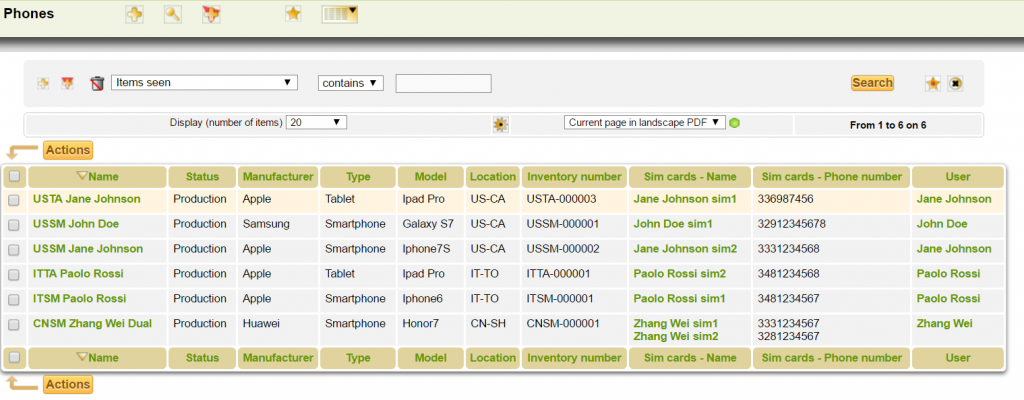
Inventory mobile devices
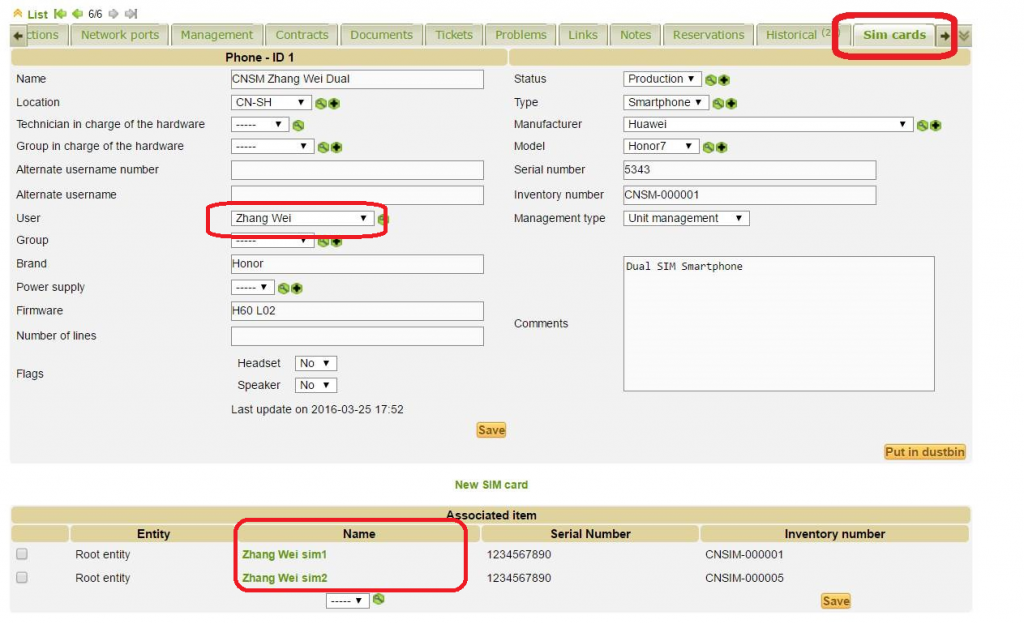
Details of a smartphone that is connected to two SIM cards
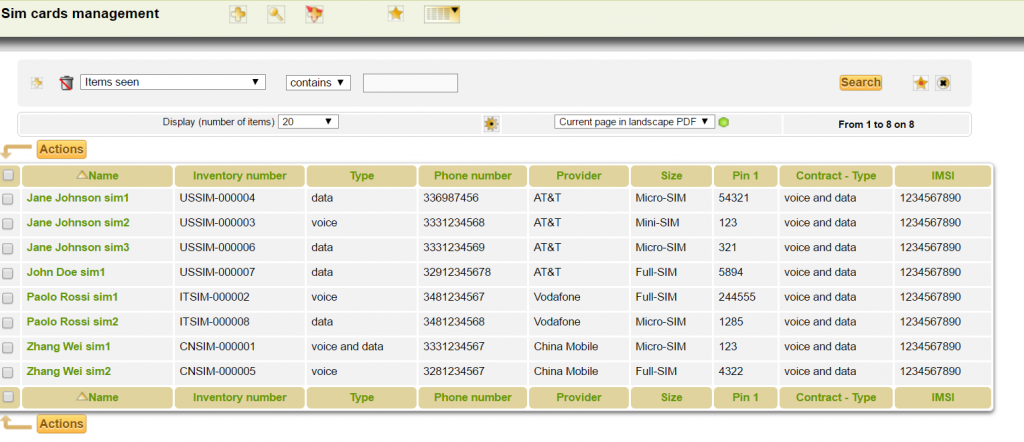
Inventory SIM cards
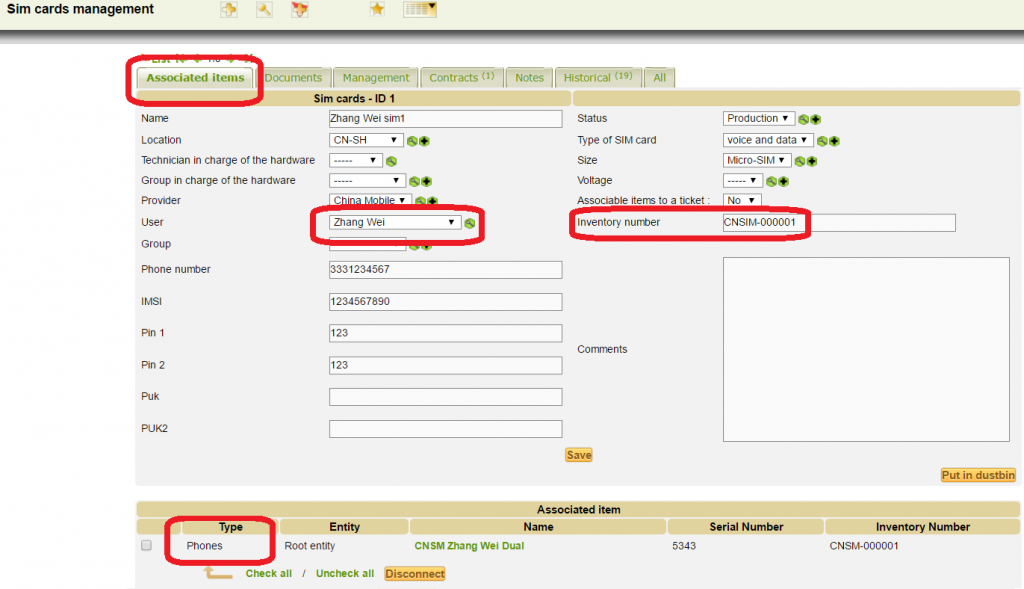
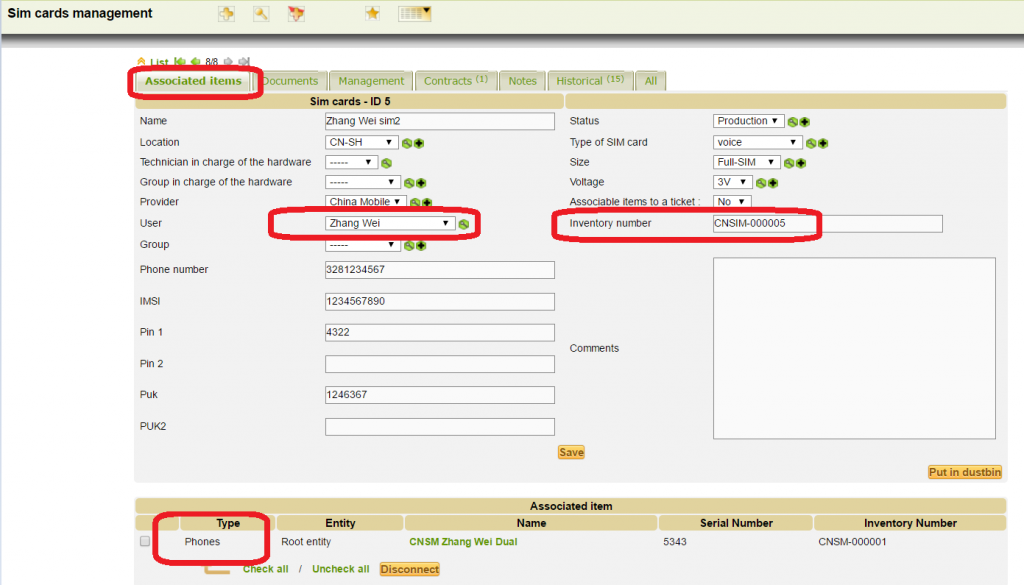
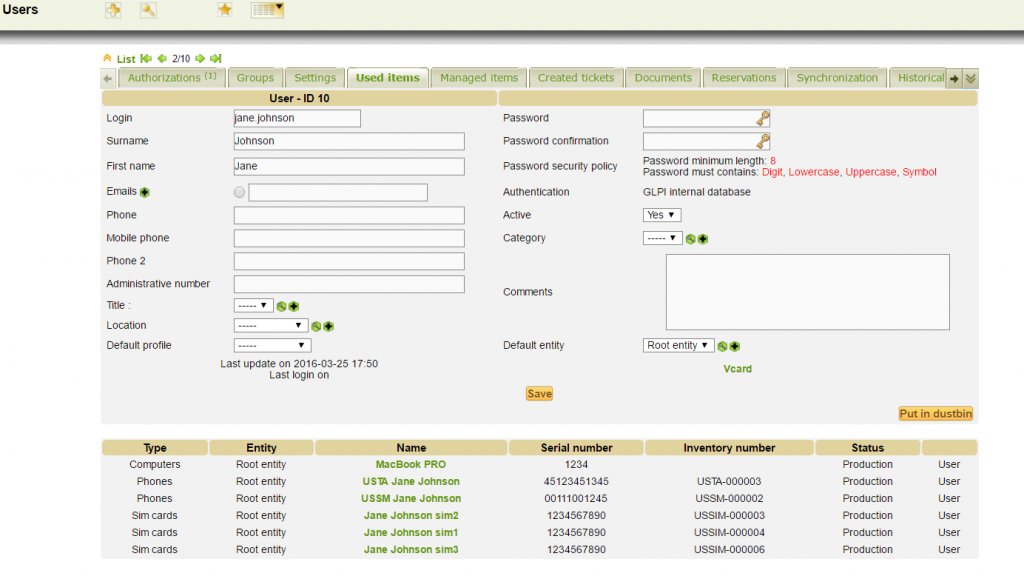
SIM card associated to a user (with dual SIM smartphone)
SIM 1
SIM 2
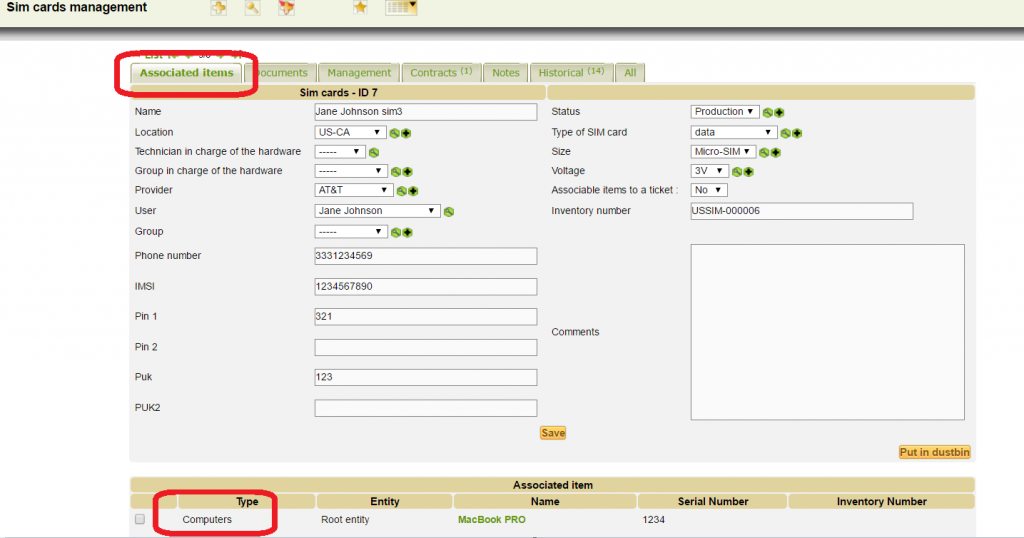
SIM card associated to a computer
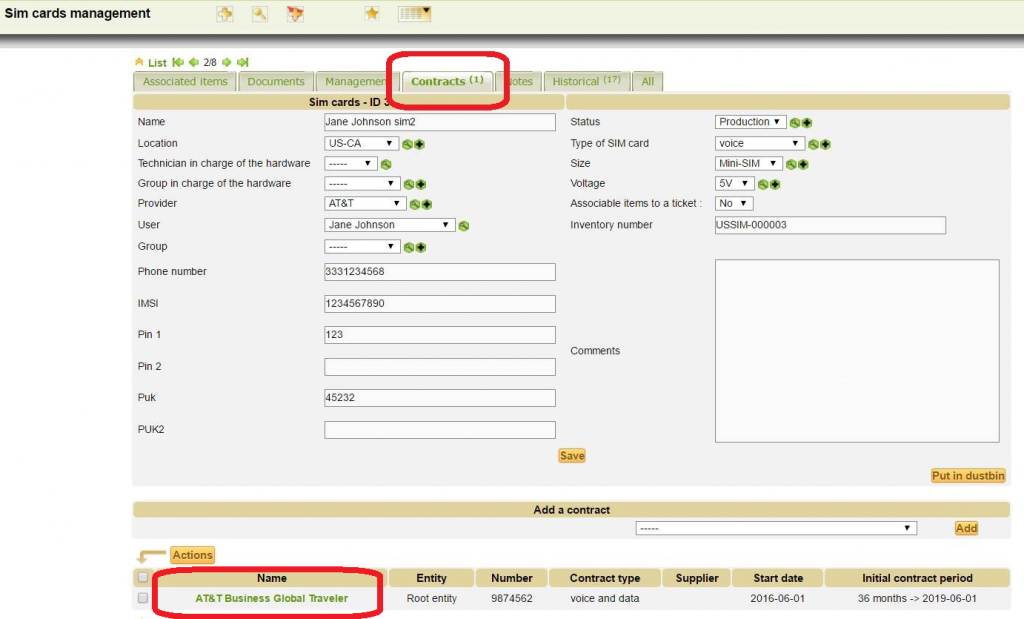
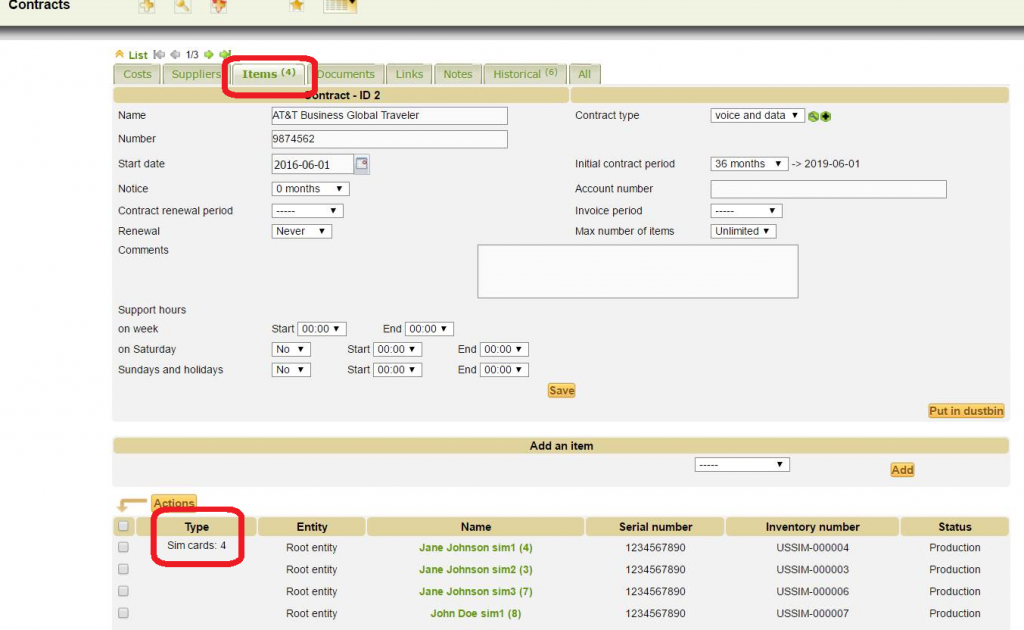
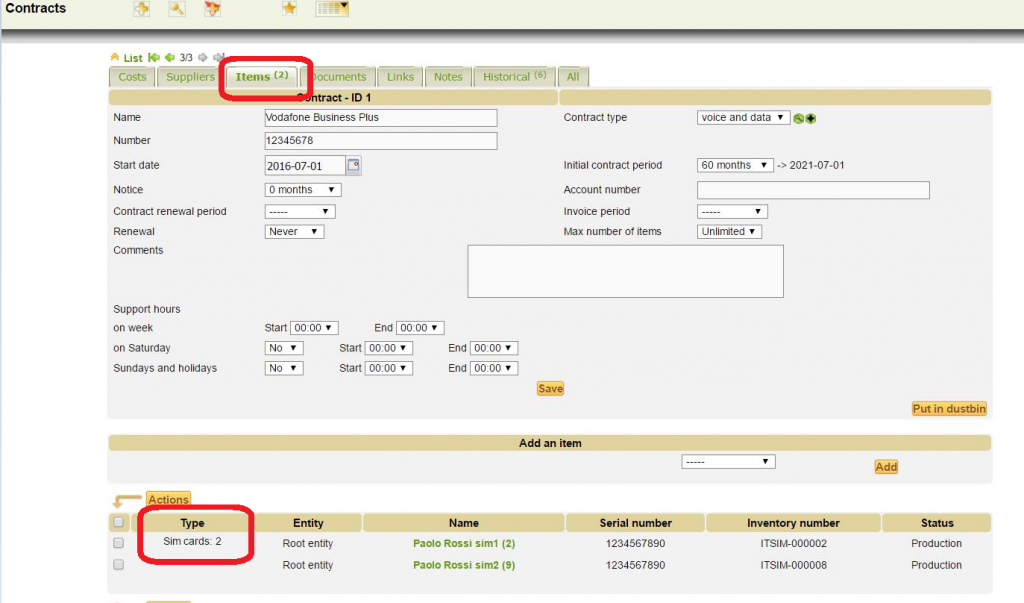
SIM card associated to a contract
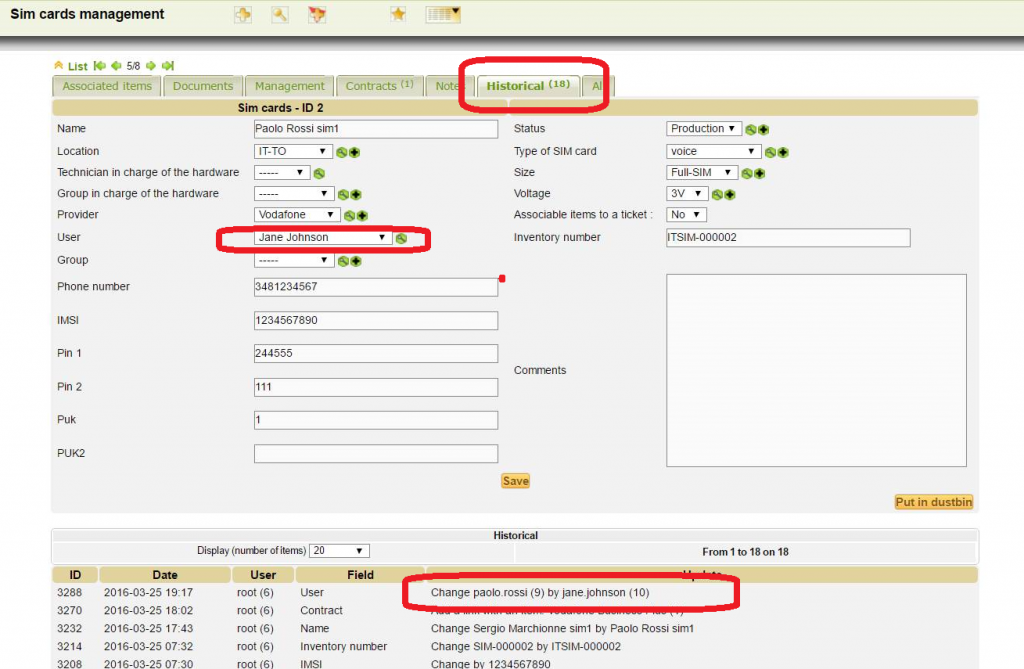
SIM card History
Elements of a contract
Elements of a user
Integration with the EriZone CMDB: visibility the assets “SIM card” and “Phone” of a user