Today’s blog article will highlight the latest news from the Syslog Server development area. The focus lays on the integration of the distributed syslog agents into the SyslogView module of the NetEye server.
The motivation for this strategic implementation is the acceleration of the installation – only a single MSI executable without user iteration has to be installed in your infrastructure – next to the deployment of the configuration for the agent.
With this feature it is possible to automatically configure and update a remotely installed SAFED agent in your infrastructure.
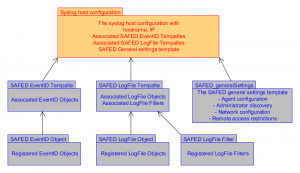
The configuration structure
The configuration of a SAFED agent consists of an architecture of three sections:
- Microsoft EventLog auditing
- Log file auditing ( text files written by applications, DBMS, etc. )
- Setup of SAFED – Server communication specific settings
As indicated in the schema below the EventID and LogFile configuration is abstracted by a templates configuration allowing the assign to a template configuration single objects.
Templates: the abstraction layer
With the introduction of an additional layer for the presentation of the configuration additional flexibility is provided.
While the single configuration object ( EventID object or LogFile object ) defines a specific event id or logfile behind a filter to monitor, the layer of the templates allows the packing of such object definitions into a logical agglomerate of of objects and filters to exclude or include.
In the same time this enables to configure an objects definition once and reuse it multiple times within templates for the various scenarios.
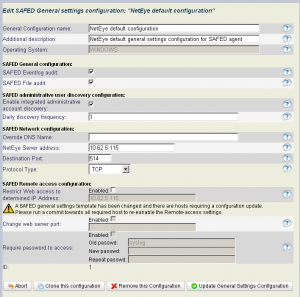
SAFED configuration profiles
The SAFED syslog agent has been developed for both the Windows and Unix/Linux world. These two worlds differ in many aspects and also the SAFED agent allows different configuration settings. For this the general settings profile differs slightly but generally trough the central configuration form we define:
- Activation of EventLog and LogFile read engine
- Local and domain wide system administrator discovery for authentication auditing
- Syslog data stream destination, port and protocol
- Security and access restriction settings
Administrator auditing
The special profile of administrator authentication auditing is realized by an integrated discovery of local and domain wide administrator accounts within SAFED. This feature audits on the Windows system the proper EventIDs for the system SAFED is installed on and enables a rule for logging of authentication activities of administrative accounts.
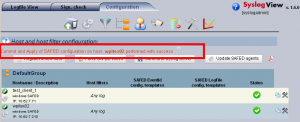
The benefit
The SAFED configuration architectures can be defined by logical host and service groups and assigned via remote commit to the remote agent. The benefit lays in the flexibility to update and extend configuration settings and to update the remote agents with a single action. Every update on the abstracted configuration structures is highlighted on the interested servers indicating the requirement for an configuration update.