31. 03. 2025
NetEye, Service Management
Snort, sistema open source di network intrusion prevention sviluppato salla Sourcefire, è il più utilizzato sistema IDS/IPS a livello internazionale.
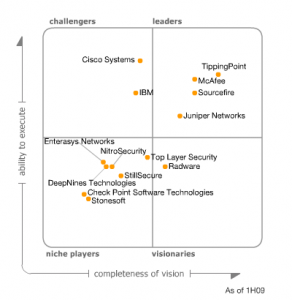
Nel Magic Quadrant Network Intrusion Prevention System della Gartner, Sourcefire si posiziona tra i leaders in base all’abilità di esecuzione e completezza di visione.
I principali punti di forza di Sourcefire, elencati dalla Gartner, sono risultati essere:
- Real time Network awareness e real time user awareness
- Utilizzo di Snort come motore di intrusion detection
- Visibilità di ciò che sta all’interno dei rules (workflow customizzabili, supporto tecnico avanzato)
- Elevata flessibilità e scalabilità
Anche in NetEye abbiamo integrato già da tempo Snort come network detection system e nell’arco del prossimo anno prevediamo di migliorare e potenziare ulteriormente il modulo di Security management per rispondere alla crescente richiesta di sicurezza da parte dei nostri clienti.
Latest posts by Arianna Cunaccia
27. 10. 2020
Events
NetEye User Group 2020
27. 10. 2020
Webinar
Cyber Security with ntopng and nScrub