Network Performance Monitoring: Port Mirroring vs. Network TAPs vs. Hardware Timestamp
Monitoring network traffic was initially used only for highlighting the typology of network traffic and the quantity of packages/bites broadcasted. This information are important to analyze anomalies, to optimize flows (balance network traffic) and to size the infrastructure.
Usually, the NetFlow protocol is used to collect network traffic data. NetFlow can be generated from the network device itself – if the device has this functionality – or from an ad-hoc device such as the nBox. The latter is recommended as it prevents a burgeoning workload of the device. Moreover, the nBox does not sample the data neither does it aggregate data every 5 minutes, as it usually happens when using network devices. When using an nBox, port mirror is used to duplicate traffic data and to send it to the probe.
Port Mirroring
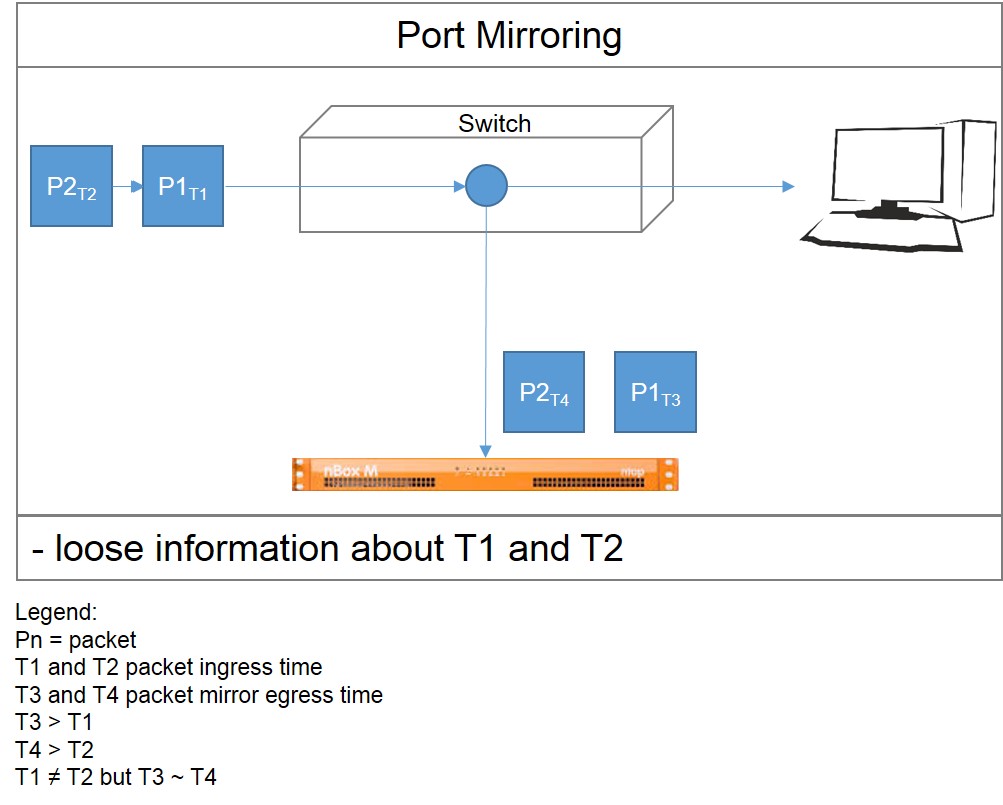
For a quantitative analysis of network traffic data port mirroring is enough, since the most important thing is that the packages are sent to the probe by a fair time.
However, new network performance monitoring systems (APM, NPM) brought tighter requirements than port span and port mirror can provide. Switches need time to copy the packages and send them to the probe. The processing time of that ends up in inaccurate data. This is a real problem if you have to evaluate network latencies of modern networks (microseconds). On top of that, some network devices do not send the packages immediately to the probe: the devices queue the packages until a certain number is reached, before sending them all together to the probe. As a consequence, the temporal distance among the packages isn’t considered and the probe’s results are wrapped.
In this case it is important to consider that the packet ingress time and the packet mirror egress time are different.
We can propose two solutions for fixing it: network Tap and hardware timestamp.
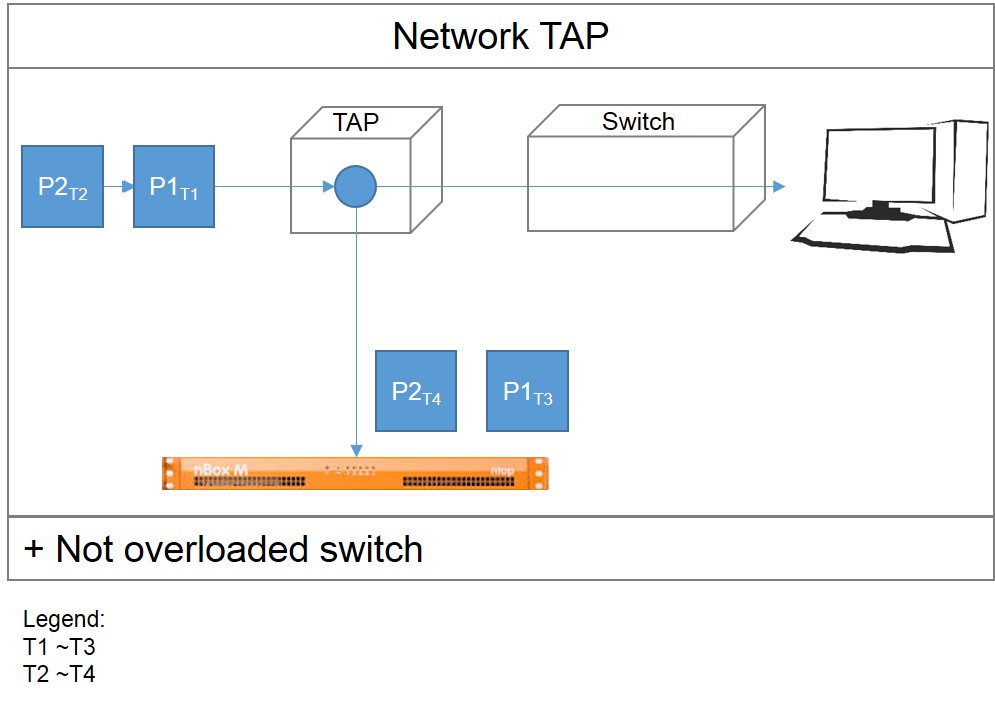
1: Network TAPs
Network TAPs are devices that mirror the traffic and immediately send it to the probe.
Network TAPs are trustworthy as they guarantee zero package loss during the mirroring (this loss might happen if you port mirror has an incorrect setup), they don’t buffer and they reduce the switches’ workload. You can find different kinds on the market, for ethernet and fiber connection, and they are a cheap alternative.
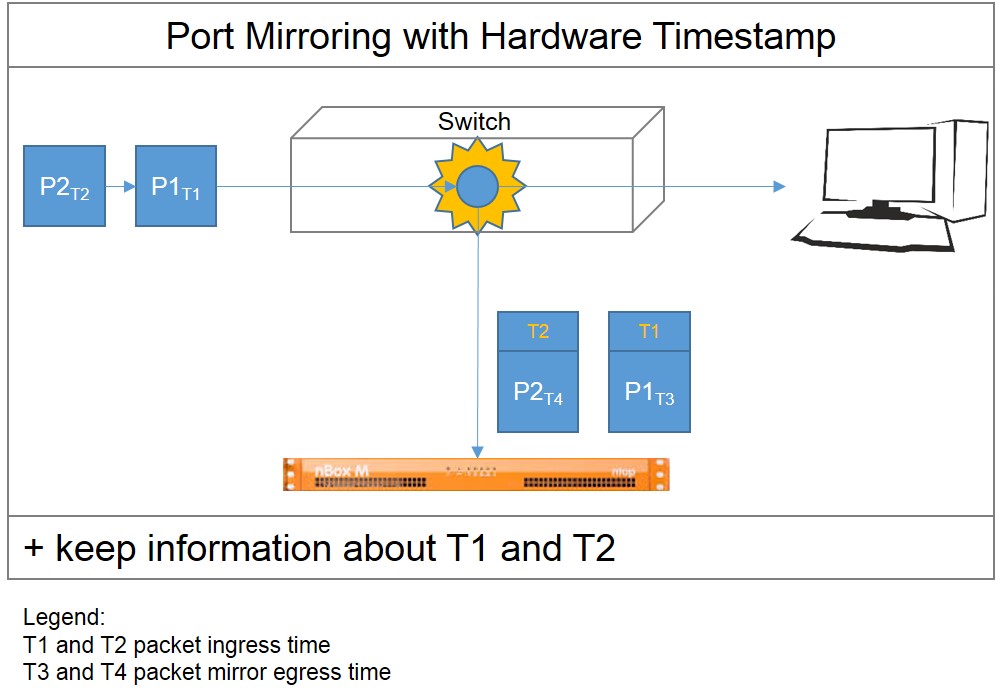
2: Hardware Timestamps
There exist also switches which apply a timestamp on the packages before queuing them up the buffering in the port mirror. The nBox is able to detect and use this (arrival) timestamp. This process eliminates all the time latencies created by the port mirror during the elaboration and the forwarding. These devices are expensive but more flexible as they provide multiple-port mirrors and allow hot configuration.
As a conclusion, port mirrors are great for IDS (intrusion detection System) and for quantitative traffic analysis and network TAPs are great for more precise network performance monitoring.